OSCP — Cracking The New Pattern
In this blog I explained how I prepared for my Exam and some of the resources that helped me pass the Exam

Hello there, I wanted to talk about how I passed OSCP new pattern, which includes Active Directory in the exam. I scheduled my exam for February 23, 2022, and passed it successfully in my first attempt. In this blog, I will try to provide all the details on my preparation strategy and what resources I utilized, so let’s dive in …
Background
I am a 20-year-old bachelor’s student at IIT ISM Dhanbad. I began my cyber security Journey two years ago by participating in CTFs and online Wargames, Later, I shifted to TryHackMe and other platforms to learn more. In September of last year, I finally decided to take the OSCP and started preparing accordingly. Before we go any further, let’s discuss the recent OSCP exam changes. If you’re already familiar with the new pattern, you may skip this part.
Recent OSCP Changes (Since Jan 2022)
The exam pattern was recently revised, and all exams after January 11, 2022 will follow the new pattern. The exam will include an AD set of 40 marks with 3 machines in the chain. Other than AD there will be 3 independent machines each with 20 marks. Additionally, the bonus marks for submitting the lab report have been doubled from 5 to 10 points, and the lab report must include an AD set writeup. I strongly advise you to read the official announcement if you are unfamiliar with the new pattern.
Preparation
I’ll go over what I did before enrolling for the OSCP that made me comfortable in going through PWK material and Labs.
Tryhackme:
Before starting the OSCP preparations, I used to solve tryhackme rooms. I generally used to solve the walkthroughs room in various categories. They explain the topic in an engaging manner.
HackTheBox:
Specifically for the OSCP, I bought the HackTheBox subscription and started solving TJNull OSCP like boxes. I highly recommend solving them before enrolling for OSCP. The best approach to complete is to solve with someone you know preparing for the same (if you are struggling to find someone, then use Infosec prep and Offensive Security Discord server to find many people preparing for OSCP and various other certifications). I converted the TJNull sheet to another sheet to keep track of the boxes I solved and tracked them together with my friend.You can find a sample copy of the sheet here.
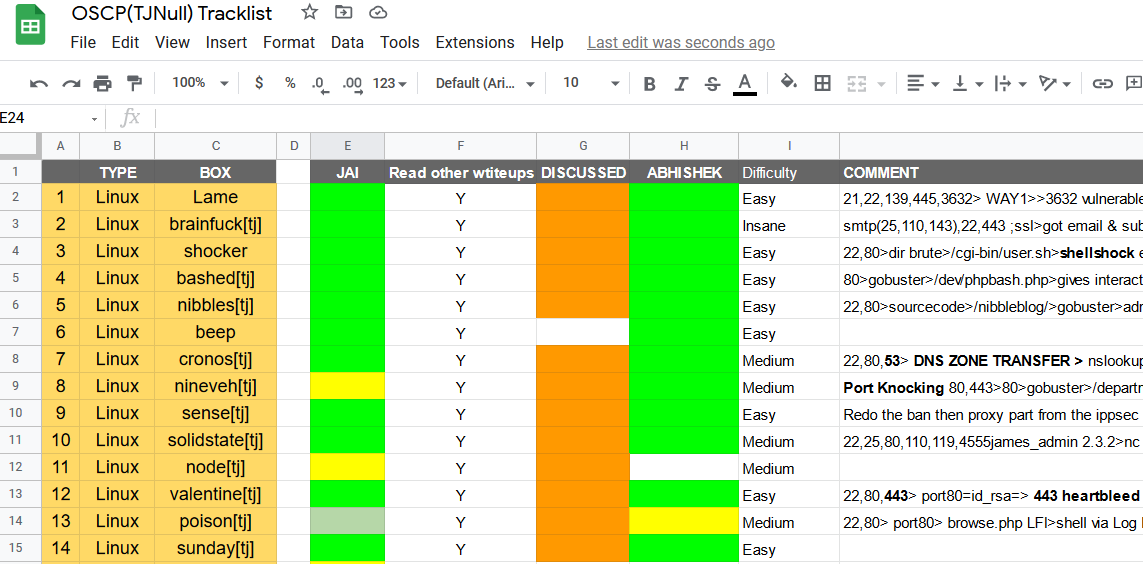
We sometimes used to solve them together, sometimes alone and then discuss our approach with each other. To avoid spoilers, we only discussed when we had both solved individually. We used to look at other blogs and Ippsec videos after solving to get more interesting approaches to solve. Watching Ippsec videos are highly recommended as he goes over everything in great depth and sometimes shows interesting manual ways to exploit. I felt comfortable with the machines after solving around 55–60 machines from Tjnull Hackthebox List, therefore I switched to PWK Labs.
Booking PWK
After 2 months of HackTheBox practice, I decided to book the PWK Labs in mid-November, which were intended to begin on December 5th, but Offensive Security updated the Exam format introducing Active Directory, which I had just heard the name of until then :(

So, in order to prepare for Active Directory, I rescheduled my lab from December 5 to December 19, giving me 15 days to prepare.
AD Preparation
The most exciting phase is about to begin. I had no idea where to begin my preparation or what to expect on the Exam at the moment. But now passing the Exam, I can tell some of the valuable resources that helped me understand AD from basics (following the order) —
- Some of the rooms from tryhackme to learn the basics- Attacktive Directory and Post-Exploitation Basics .
- The Active Directory portion of Practical Ethical Hacking The Complete-Course by TheCyberMentor. In fact, the complete course (25 hrs approx.) is worth doing in general.
- Chapter-21 Active Directory Attacks of PWK pdf that comes along with the PWK course is extremely significant from the OSCP’s perspective.
- The two active directory network chains in the PWK lab are crucial for the Exam (may expect similar machines in the Exam)
The above resources are more than sufficient for the exam, but for further practice, one can try —
- Wreath and Throwback from TryHackMe (You can also just follow Throwback walkthrough by John Hammond Part I and Part II )
- Some of the Active Directory Machines from HackTheBox.
- Hutch, Hiest, Vault from Proving Grounds provided by Offensive Security itself.
Practice using some the tools such as PowerView and BloodHound to enumerate Active Directory. Also, explore tools such as Impacket, Crackmapexec, Evil-winrm, Responder, Rubeus, Mimikatz. There is also a great blog on Attacking Active Directory that you should check out. I encountered the machine in the exam, which can be solved just with the knowledge of PWK lab AD machines and the material taught in the AD chapter of the manual.
PWK Labs
I took only a 1-month subscription, spent about 15 days reading the PDF and solving exercises (which were worth 10 additional points), leaving me with only 15 days to complete the labs. In that period, I was able to solve approximately 35–40 machines. I recommend solving as many boxes as possible in the lab as they are more like the real world, with some being interdependent on one another and others requiring pivoting.
BOF
Buffer overflow may or may not appear in the exam as per the new changes. If it comes, it will be a low privilege vector that will necessitate privilege escalation to achieve the full 20 points. TheCyberMentor Buffer Overflow video and TryHackMe Buffer Overflow Prep room are more than sufficient for BOF preparation.
THE EXAM
I scheduled my exam for the morning of February 23rd at 10:30 a.m., began with AD, and had an initial shell on one of the boxes in 30 minutes, but then misinterpreted something during post enumeration, resulting in wasting 5–6 hours trying to figure out something that was not required to move forward. Decided to take a long break and then compromised the whole AD set in the next 1.5 hours. If I hadn’t made that mistake, it would have taken me about 2 hours to solve the entire AD chain. Then, moving on to standalone machines, I began enumerating them one by one in order to discover low-hanging fruit, and within the following two hours, I was able to compromise another machine. Now I had 70 points (including bonus) to pass the Exam so I took a long break to eat dinner and a nap. Coming back in some time I finally established a foothold on another machine, so had 80 points by 4 a.m. in the morning; I was even very close to escalating the privileges but then decided to solve AD once again and take some missing screenshots. I finished my Exam at about 8 a.m., after documenting other solved standalone machines. Took a long sleep, finally woke up at night, submitted the report, and received a congrats email in the next 24 hours.

In the Exam, I would recommend dedicating a set amount of time to each machine and then moving on, returning later. Take a break to calm down and reset your thoughts if you’re stuck somewhere and don’t know what to do. Now start it fresh with a broader enumeration, making a note of any juicy information that may help later on. There might be something we missed in enumeration the first time that could now help us move forward.
Conclusion
I would like to thank my family and friends for supporting me throughout this Journey. This would not have been possible without their encouragement and support. If you’ve made it this far, you’re probably interested in the certification, therefore I wish you Goodluck on your OSCP journey. Ping me on Linkedin if you have any questions. Stay tuned for additional updates; I’ll be publishing my notes that I made in the past two years soon. Also, subscribe to my Youtube channel, where I will begin posting security-related videos.
Connect with me on Twitter, Linkedin, Youtube.
Other Helpful Resources
These are some of the resources that I found helpful during my preparations:
- https://book.hacktricks.xyz/ (have almost everything that you need)
- https://viperone.gitbook.io/pentest-everything/
- https://gtfobins.github.io/ (useful in Linux Privilege escalation)
- SecWiki/windows-kernel-exploits
- https://github.com/swisskyrepo/PayloadsAllTheThings
- https://addons.mozilla.org/en-US/firefox/addon/hacktools/ (very useful has cheatsheet in the form of extension)
- https://docs.google.com/spreadsheets/d/1cDZpxrTMODHqgenYsBuZLkT-aIeUT31ZuiLDhIfrHRI/edit?usp=sharing (Link to my Box Tracklist)
- https://academy.tcm-sec.com/?affcode=770707_iixyvfcq
Recently Offensive Security also published a video talking about the new Exam pattern in detail.
Thanks for your patience,I hope you enjoyed reading. Happy Hacking…