A4 - Insecure Direct Object References(IDOR) | Solutions of bWAPP | Walkthrough of All Levels
Writeups of all levels in A4 - Insecure Direct Object References Catagory such as Solutions of Insecure DOR (Change Secret), Insecure DOR (Reset Secret), Insecure DOR (Order Tickets).
Here is a walkthrough and tutorial of the bWAPP which is a vulnerable web application by itsecgames which you can download and test on your local machine. It has a complete list of OWASP vulnerabilities which we can practially test. The best part of using bWAPP is that it is running on our local system so we have access to its source code, so if we got stuck somewhere then we can analyse its source code as it is very neat and describitive having comments wherever necessary. We can see the function being used to restrict or sanatize the input,then can search for its vulnerablity on the web.
Hello, today we are going to solve Insecure Direct Object Reference (IDOR) of Buggy Web Application such as Insecure DOR (Change Secret), Insecure DOR (Reset Secret), Insecure DOR (Order Tickets).
Insecure DOR (Change Secret)
Security Level: low
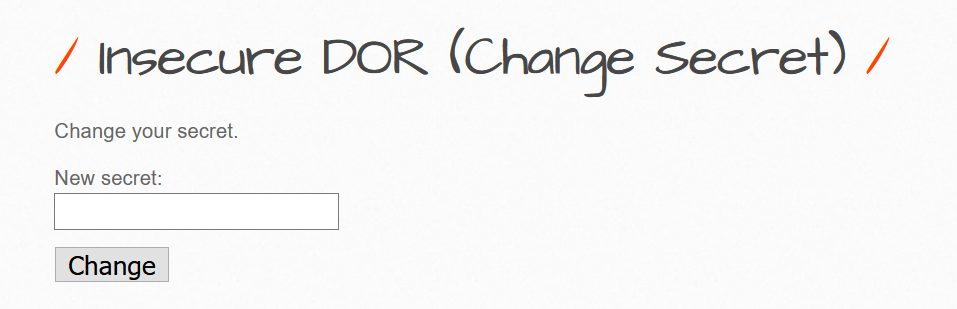
Simply a text box, asking for the new secret key.
Intersepting request provide us the username of the logged in user which can be modified,
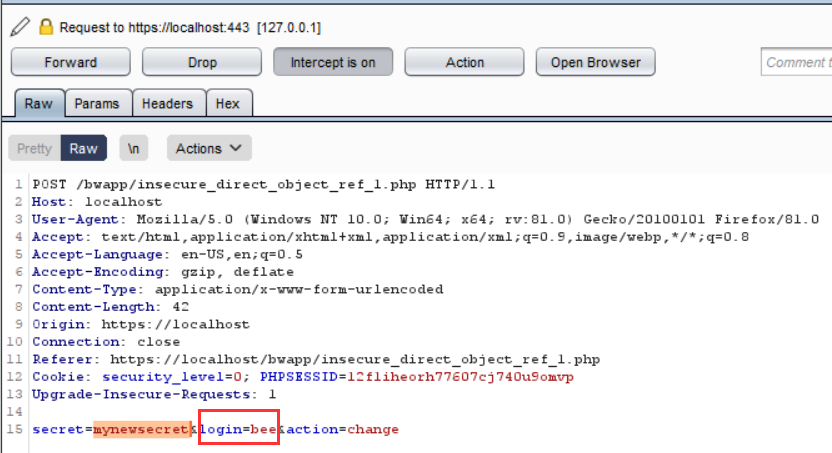
Now if we know the username of any other user then we can modify the request to make changes in someone else account whose account access we don’t have.

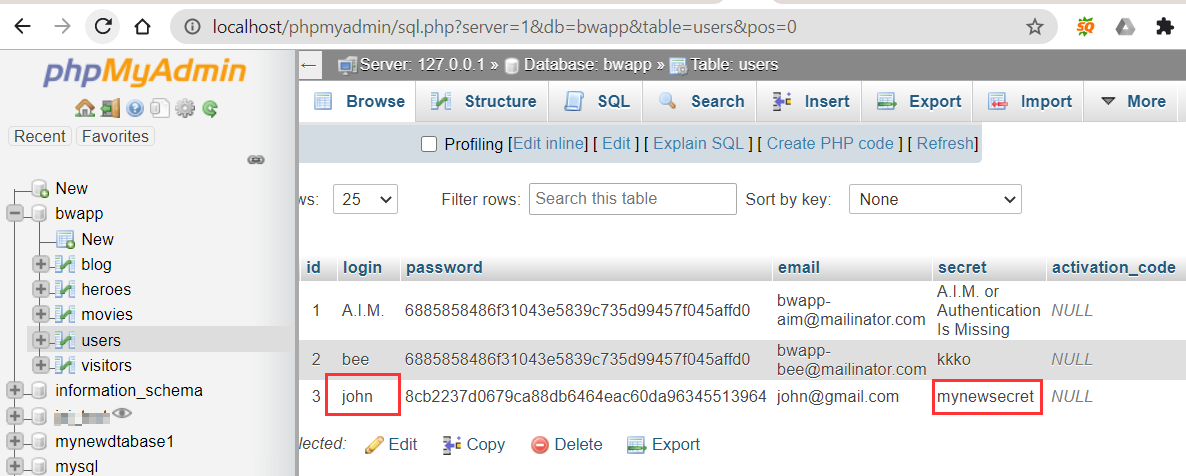
Like here we changes it to that of john to add this secret to john’s accounts, but for this there mmust be a user name john. Now if we take a look at the mysql database we can see that we have changes the secret of john account from bee’s account.
If we look at the source code we can see that there is no condition or validation except character filter.
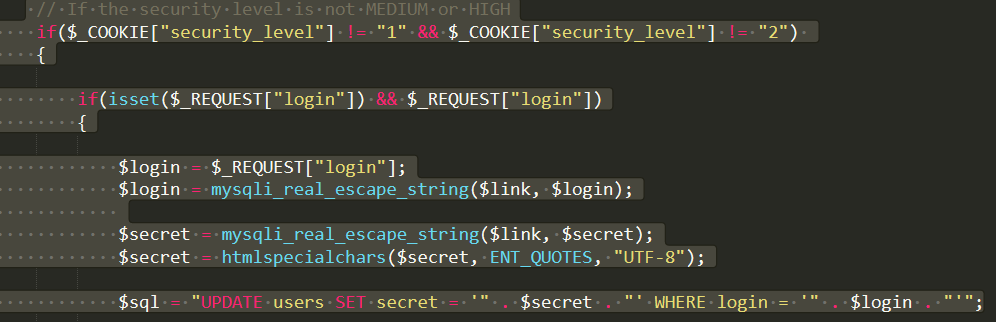
Security Level: medium/high
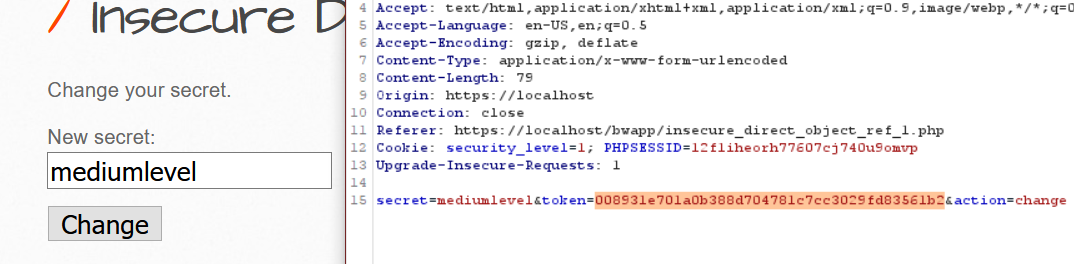
Trying the same but this time No login parameter in the request rather it is assigning unique random token to each user in each request to prevent data tempering.
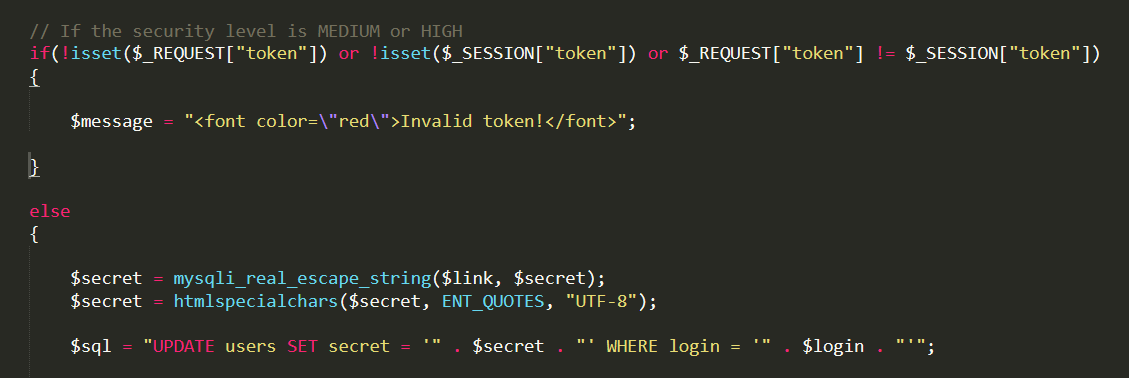
If we see the code we can see that it is validating each request:
Under Contruction!!!!!!
/Thanks for your patience, I hope you enjoyed reading. Happy Hacking… /